Description
This article describes how to solve Radius most common problems.
Solution
To test the Radius object and see if this is working properly, use the following CLI command:
#diagnose test authserver radius <radius server_name> <authentication scheme><username> <password>
Note:
<Radius server_name> = name of Radius object on Fortigate.The authentication scheme could be one of the following: Pap, Chap, mschapv2, mschap.Example:
#diagnose test authserver radius Radius_SERVER pap user1 password
Advanced troubleshooting:
To get more information regarding the reason of authentication failure, use the following CLI commands:
# diagnose debug enable
# diagnose debug application fnbamd 255
To stop this debug type:
#diagnose debug application fnbamd 0
And then run a LDAP authentication test:
#diag test authserver radius RADIUS_SERVER pap user1 password
Advanced troubleshooting:
#diag test authserver radius FAC_RADUIS pap user1 Password
handle_req-Rcvd auth req 237264669 for user1 in FAC_RADUIS opt=0000001d prot=0
compose_group_list_from_req-Group ‘FAC_RADUIS’
fnbamd_pop3_start-user1
fnbamd_cfg_get_radius_list_by_server-Loading RADIUS server ‘FAC_RADUIS’
fnbamd_create_radius_socket-Opened radius socket 15
fnbamd_create_radius_socket-Opened radius socket 16
fnbamd_radius_auth_send-Compose RADIUS request
fnbamd_rad_dns_cb-192.168.1.99
fnbamd_rad_send-Sent radius req to server ‘FAC_RADUIS’: fd=15, IP=192.168.1.99(192.168.1.99:1812) code=1 id=164 len=91 u=»user1″ using Pap <—— Username and authentication scheme.
radius_server_auth-Timer of rad ‘FAC_RADUIS’ is added
create_auth_session-Total 1 server(s) to try
fnbamd_auth_handle_radius_result-Timer of rad ‘FAC_RADUIS’ is deleted
fnbamd_radius_auth_validate_pkt-RADIUS resp code 2
extract_success_vsas-FORTINET attr, type 1, val AdminGroup
fnbamd_auth_handle_radius_result—>result for radius svr ‘FAC_RADUIS’ 192.168.1.99(1) is 0 <—— 0: authentication success; 1: authentication failed.
authenticate ‘user1’ against ‘pap’ succeeded, server=primary assigned_rad_session_id=237264669 session_timeout=0 secs idle_timeou secs!
Group membership(s) — AdminGroup
Radius Response codes in the Fnbamd Debug:
0: Success
1: Deny
2: Challenged (password renewal or token is needed)
3: unknown
4: Pending
5: Error
6: Framed IP Conflict
7: Token code is required
8: Need another token due to the previous one is out of sync
9: Response Buffer is too small
10: Authentication time out
11: Max Concurrent authentication sessions are reached
12: Token code is already used.
Here it is also possible to see usual(error) mschapv2 codes:
646 ERROR_RESTRICTED_LOGON_HOURS
647 ERROR_ACCT_DISABLED
648 ERROR_PASSWD_EXPIRED
649 ERROR_NO_DIALIN_PERMISSION
691 ERROR_AUTHENTICATION_FAILURE
709 ERROR_CHANGING_PASSWORD
If a packet capture is done, using (# diag sniffer packet any «host x.x.x.x» 6 0 a) or Wireshark, here is the reference for RADIUS codes:
| Code | Assignment |
|---|---|
| 1 | Access-Request |
| 2 | Access-Accept |
| 3 | Access-Reject |
| 4 | Accounting-Request |
| 5 | Accounting-Response |
| 11 | Access-Challenge |
| 12 | Status-Server (experimental) |
| 13 | Status-Client (experimental) |
| 40 | Disconnect-Request |
| 41 | Disconnect-ACK |
| 42 | Disconnect-NAK |
| 43 | CoA-Request |
| 44 | CoA-ACK |
| 45 | CoA-NAK |
| 255 | Reserved |
This is a guide illustrating how to troubleshoot communication between your router (Mikrotik example) and the Radius server (Splynx).
Video tutorial for Radius configuration:
Step 1
Firstly make sure that the router is accessible from Splynx and vice versa that the router can «reach» Splynx. In Splynx you can check the reachability with a ping status from Splynx to the router:
This troubleshooting step is only suitable when the «ping» (ICMP traffic) is not restricted between the router and the Splynx server (If ICMP echo responses are not blocked/filtered on the firewall).
Also read these manuals and compare the settings to ensure that setup is correct:
-
in case of using PPPOE with Radius follow this: PPPoE with RADIUS
-
in case of using DHCP with RADIUS (IPoE) follow this: DHCP with RADIUS
Step 2
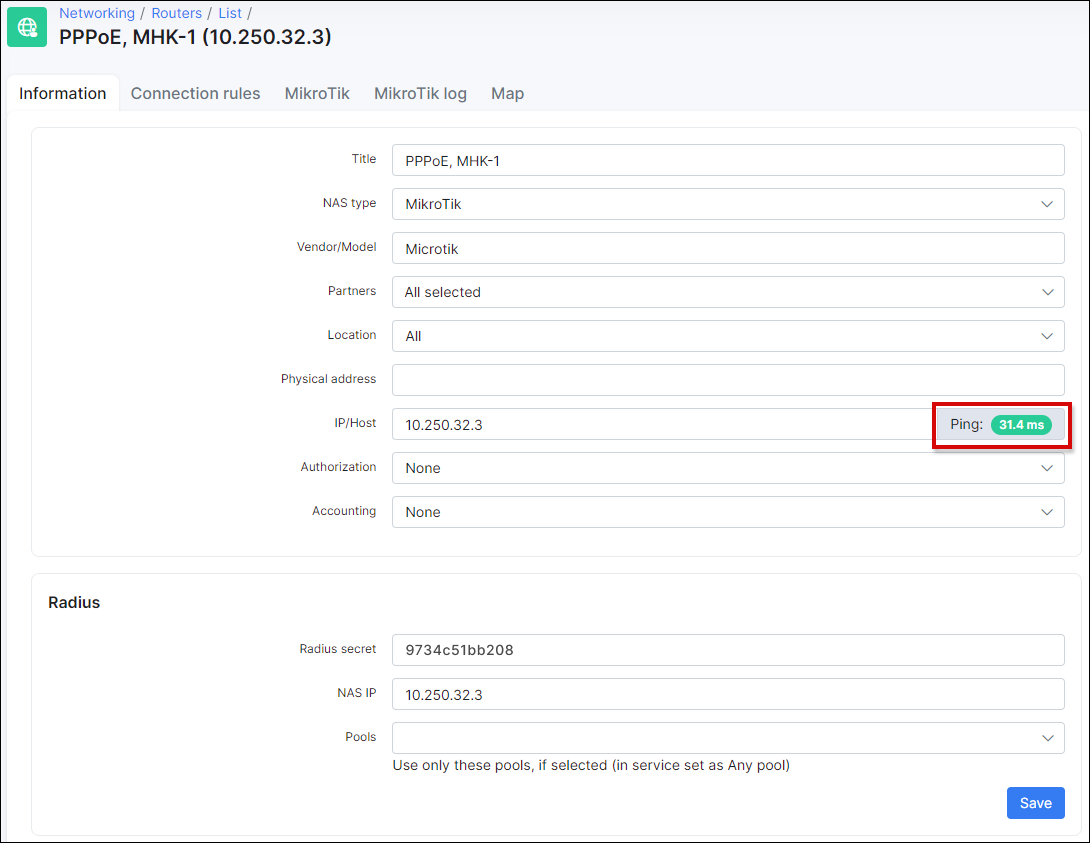
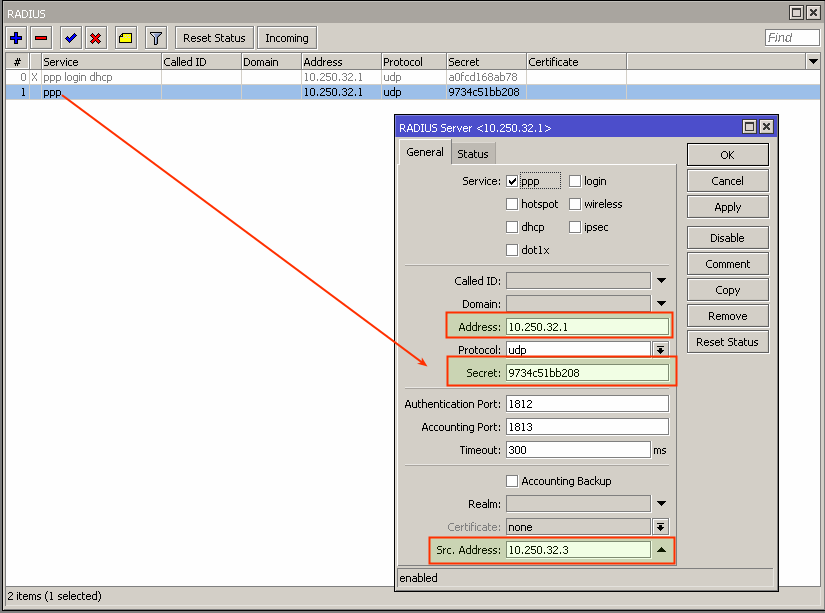
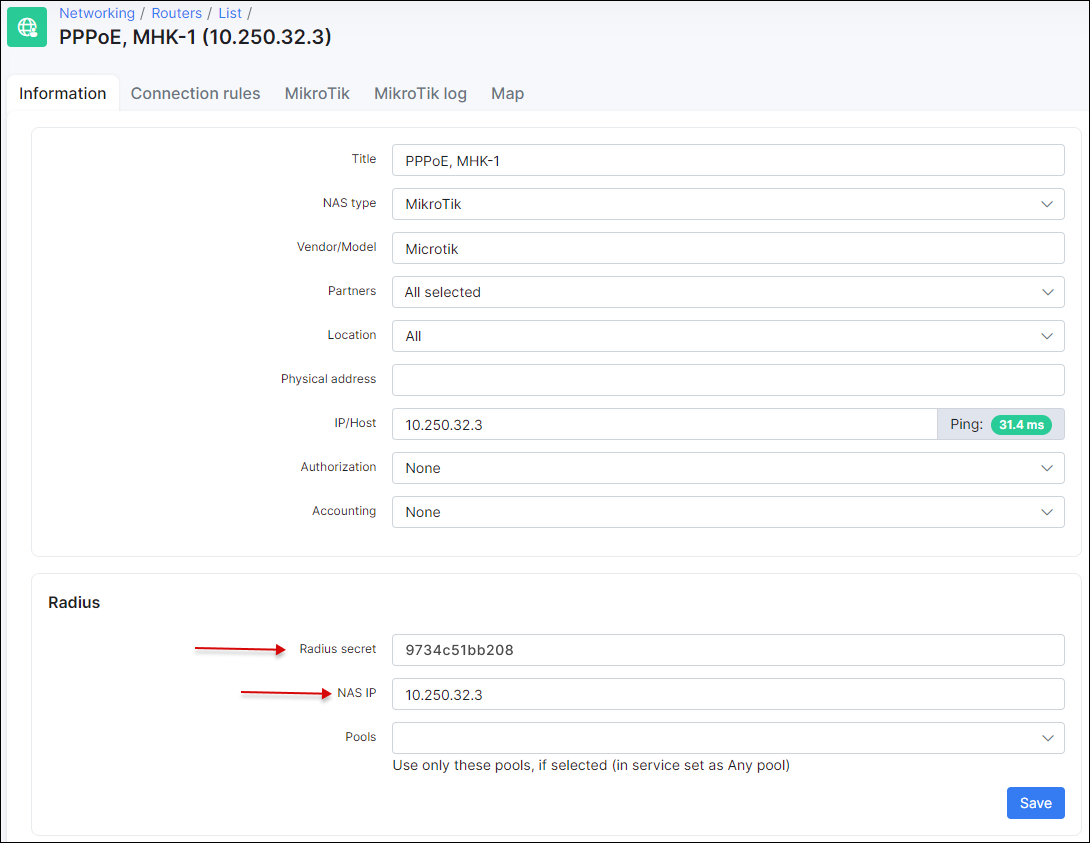
Compare RADIUS parameters on the router information tab in Splynx and on the Mikrotik router under the RADIUS menu:
The Secret field on the Mikrotik should be the same as field Radius secret on the router in Splynx.
The IP Address field on the Mikrotik should be filled with Splynx’ IP.
The Src.Address field on Mikrotik should be filled with the router IP or can be 0.0.0.0.
The NAS IP field in Splynx is the real source IP address for RADIUS packets. It is recommended that in the Radius settings of the Mikrotik router Src. address equals NAS IP in Splynx.
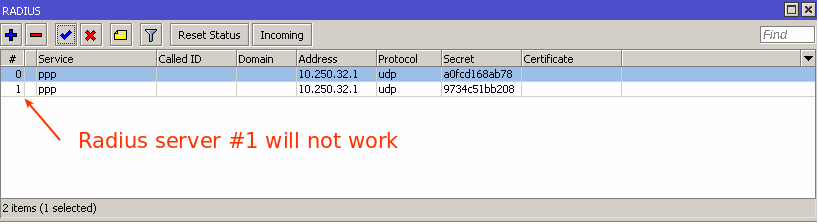
Also make sure that you don’t have multiple RADIUS servers configured with same services:
You can have multiple RADIUS servers however each server should be configured with unique services, for example: RADIUS server #1 configured for DHCP service, RADIUS server #2 configured for PPP service.
Step 3
Check the firewall and ports. RADIUS is transported over UDP on ports 1812 (authorization) and 1813 (accounting) so these 2 ports should be open on the router as well as port 3799 (radius incoming) should be open and not blocked by any firewall rules/filters.
Step 4
Inspecting of logs.
By default Splynx writes logs into 2 files: coa.log and short.log that you can find in the folder /var/www/splynx/logs/radius on CLI or via the web interface, navigate to Administration → Logs → Files and search these 2 files.
The short.log file will display all records of login attempts, the reason of disconnection. For example:
28/02 14:54:16:7361 - [Login ] - [10.2.32.109 ] - Accept
28/02 14:54:23:3637 - [C38F676DB15B ] - [10.2.36.0 ] - Log in
28/02 14:54:18:6727 - [C38F676DB15B ] - [10.2.33.190 ] - Log off - (NAS-Error)
28/02 14:54:19:3702 - [26117AB65E2B ] - [10.2.36.0 ] - Log off - (Session-Timeout)
28/02 14:54:22:7030 - [-Unknown- ] - [10.250.74.24 ] - Reject (ATTR + IP accept) - [26117AB65E2B] -> [service1] Customer not found
28/02 14:54:23:2525 - [26117AB65E2B ] - [10.2.33.190 ] - Reject (Attribute accept) - [FCACAF943B30] -> [service1] Customer is not active
28/02 14:54:14:2384 - [user ] - [10.2.36.247 ] - Reject - [B4FBE4ACFCC2] -> [service1] Customer is already online
28/02 14:54:21:2743 - [265798031 ] - [ ] - [card] Accept
28/02 14:54:21:5017 - [265798031 ] - [10.5.28.211 ] - [card] Log in
28/02 15:10:35:6518 - [voucher-login ] - [10.1.0.202 ] - [card] Log off - (User-Request)
28/02 15:11:05:2315 - [serieALRClM4sj ] - [ ] - Reject card - [4FFE0CD555D3] -> [hap-lite] Password is incorrectThis file contains the following information: date and time, login of the service, IP and description of action.
Descriptions of records:
- Accept — The Splynx server received the Radius-Access Request packet from the Router and a Radius Access-Accept packet was sent back. Customer was successfully authenticated. Please note, if MS-CHAP is used for authentication, we can see
Accepthere even if password is incorrect; - Log in — The Splynx server received the Radius Accounting-Start packet from Router;
- Log off — The Splynx server received the Radius Accounting-Stop packet from Router;
- Reject — The Splynx server received the Radius Access-Request packet from Router and Radius Access-Reject was sent back. Customer was not authenticated;
- Reject (Attribute accept) — The Splynx server sent the Radius Access-Accept packet to Router with the IP address from the Splynx service. Customer was authenticated on the router with a session time limit = Config → Networking → Radius → Error session time limit. IP address was added into the Address list
Reject_xon the router; - Reject (ATTR + IP accept) — The Splynx server sent the Radius Access-Accept packet to the Router with an IP address from the Splynx Reject pool (Config → Networking → Radius → Reject IP x). Customer was authenticated on the router with session time limit = Config → Networking → Radius → Error session time limit. IP address was added into the Address list
Reject_xon the router; - [card] Accept — The same as Accept but for Prepaid vouchers.
- [card] Log in — The same as Log in but for Prepaid vouchers.
- [card] Log off — The same as Log out but for Prepaid vouchers.
- Reject card — The same as Reject but for Prepaid vouchers.
In the case of authentication errors or logging off, the reasons are shown in the radius logs under Administration → Logs → Files → radius/short as well as in the customer statistics under sessions (enable the «Termination cause» column).

short.log like Admin-reset or Lost-carrier are not related to Splynx and should be investigated on the network.
In the coa.log you can find records that can help you with troubleshooting of issues with disconnection, plan change etc. If Splynx sends a CoA packet, it will be logged here:
2021-10-07 07:15:02 - echo "User-Name = mike, Framed-IP-Address = 192.168.200.218, NAS-IP-Address = 10.250.32.3" | /usr/bin/sudo /usr/bin/radclient 10.250.32.3:3799 disconnect "9734c51bb208" > /dev/null &
2021-10-07 07:15:49 - echo "User-Name = mike, Framed-IP-Address = 192.168.200.28, NAS-IP-Address = 10.250.32.3" | /usr/bin/sudo /usr/bin/radclient 10.250.32.3:3799 disconnect "9734c51bb208" > /dev/null &
2021-10-07 07:20:10 - echo "User-Name = mike,Framed-IP-Address = 192.168.200.108, NAS-IP-Address = 10.250.32.3 , Mikrotik-Rate-Limit = "5000000/5000000 0/0 0/0 0/0 5 5000000/5000000"" | /usr/bin/sudo /usr/bin/radclient 10.250.32.3:3799 coa "9734c51bb208" > /dev/null &
2021-10-07 07:32:46 - echo "User-Name = mike, Framed-IP-Address = 192.168.200.137, NAS-IP-Address = 10.250.32.3" | /usr/bin/sudo /usr/bin/radclient 10.250.32.3:3799 disconnect "9734c51bb208" > /dev/null &
2021-10-07 07:45:37 - echo "User-Name = mike, Framed-IP-Address = 192.168.200.5, NAS-IP-Address = 10.250.32.3" | /usr/bin/sudo /usr/bin/radclient 10.250.32.3:3799 disconnect "9734c51bb208" > /dev/null &
2021-10-07 11:45:10 - echo "User-Name = mike,Framed-IP-Address = 192.168.200.5, NAS-IP-Address = 10.250.32.3 , Mikrotik-Rate-Limit = "10000000/10000000 0/0 0/0 0/0 5 1000000/1000000"" | /usr/bin/sudo /usr/bin/radclient 10.250.32.3:3799 coa "9734c51bb208" > /dev/null &
In this part of the coa.log you can see that Splynx has sent some CoA packets to disconnect a user and change the speed of the connection.
The Splynx Radius server consist of 2 services: splynx_radd and freeradius. Both of them have different debugging procedures and show different information. Let’s start with the splynx_radd debug:
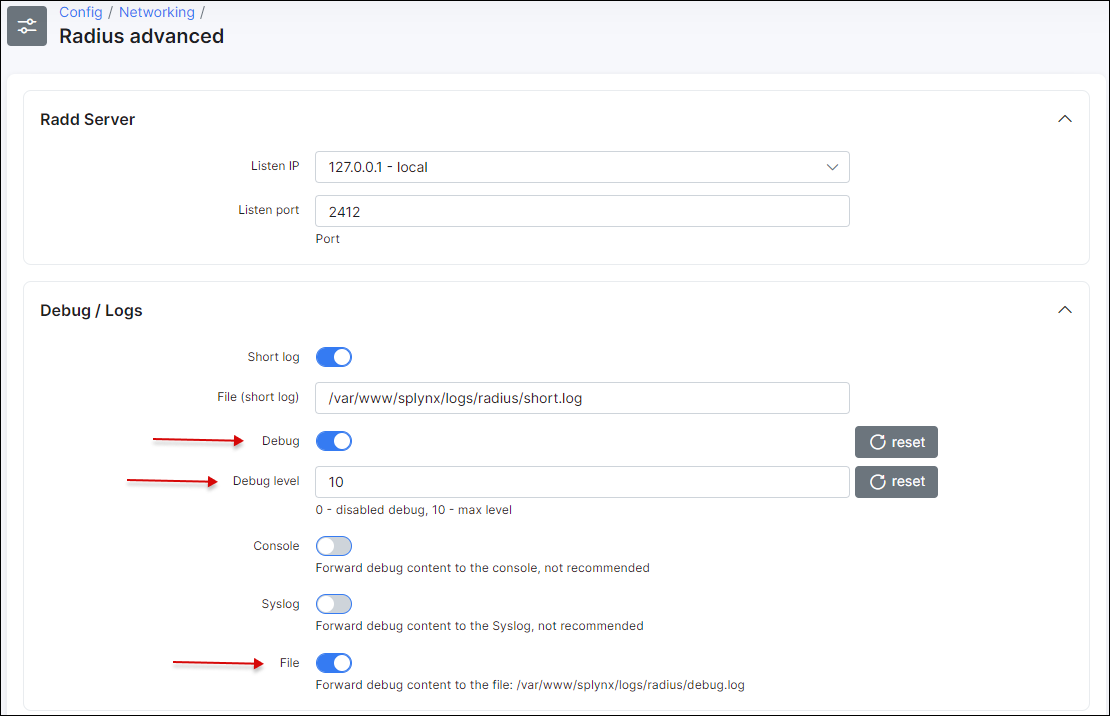
To enable debug mode for splynx_radd, navigate to Config → Networking → Radius advanced and enable debug (change the level of debug to get more or less detail in the log):
Apply new settings immediately by saving and restarting the Radius server.
To restart Radius server use the button at the bottom of the same page (Config → Networking → Radius advanced), or enter command in SSH:
service splynx_radd restartNow we can check the debug file. It is also accessible from the CLI of Linux Splynx server:
/var/www/splynx/logs/radius/debug.log
The best way to check the file is by using the tail command:
tail -f /var/www/splynx/logs/radius/debug.logOnce the debug is completed, remember to switch the debug off the same way it was switched on, save and restart the radius server again. (To avoid massive radius rebug files forming)
If splynx_radd debug doesn’t show us the desired results, we can also run freeradius daemon in debug mode and see if any packets are received by Radius server.
Run CLI commands to get output into the file:
service freeradius stop && freeradius -Xxxx | tee Debugxxx.logWait for 2-5 minutes to collect some data and stop execution of this command by using Ctrl+C and start freeradius in a regular mode:
service freeradius startIf the freeradius daemon returns an error after the last command run this:
killall freeradius; service freeradius restartIf you don’t see any debug messages when a customer tries to connect to the Mikrotik Router, it means that your router’s radius packets are not reaching the Splynx Radius server at all. You need to verify networking, routing and NAT settings of the network.
The use of a VPN in any case where connectivity or NATting is an issue is highly recommended and can be setup natively in Splynx via the GUI:
Our guide on OpenVPN and OpenVPN client / Routes
On the Mikrotik Router there is also the ability to run extended debug to see exactly what the router is sending to the Radius server:
For more information on how RADIUS works, please visit Radius Wikipedia or FreeRADIUS Wiki
Hi,
We have struggled for a while with RADIUS auth for some clients against an NPS Server when the user or computer tries to connect to the wireless network the following error can be seen on the NPS server:
Network Policy Server discarded the request for a user
Contact the Network Policy Server administrator for more information.
User:
Security ID: NULL SID
Account Name: host/hostname.domainname.com
Account Domain: —
Fully Qualified Account Name: —
Client Machine:
Security ID: NULL SID
Account Name: —
Fully Qualified Account Name: —
OS-Version: —
Called Station Identifier: 40-20-B1-F4-BB-15:Wireless-SSID
Calling Station Identifier: C1-18-85-08-10-E1
NAS:
NAS IPv4 Address: 192.168.10.10
NAS IPv6 Address: —
NAS Identifier: AP name
NAS Port-Type: Wireless — IEEE 802.11
NAS Port: 0
RADIUS Client:
Client Friendly Name: name
Client IP Address: 192.168.10.10
Authentication Details:
Connection Request Policy Name: Secure Wireless Connections
Network Policy Name: —
Authentication Provider: Windows
Authentication Server: NPS servername
Authentication Type: —
EAP Type: —
Account Session Identifier: —
Reason Code: 3
Reason: The RADIUS Request message that Network Policy Server received from the network access server was malformed.
——————————————————————————————————————————
Network Policy Server discarded the request for a user.
Contact the Network Policy Server administrator for more information.
User:
Security ID: NULL SID
Account Name: domainnameusername
Account Domain: —
Fully Qualified Account Name: —
Client Machine:
Security ID: NULL SID
Account Name: —
Fully Qualified Account Name: —
OS-Version: —
Called Station Identifier: 20-18-B1-F4-BB-15:Wireless-SSID
Calling Station Identifier: 09-3E-8E-3E-5A-C9
NAS:
NAS IPv4 Address: 192.168.10.10
NAS IPv6 Address: —
NAS Identifier: AP name
NAS Port-Type: Wireless — IEEE 802.11
NAS Port: 0
RADIUS Client:
Client Friendly Name: name
Client IP Address: 192.168.10.10
Authentication Details:
Connection Request Policy Name: Secure Wireless Connections
Network Policy Name: —
Authentication Provider: Windows
Authentication Server: NPS server name
Authentication Type: —
EAP Type: —
Account Session Identifier: —
Reason Code: 3
Reason: The RADIUS Request message that Network Policy Server received from the network access server was malformed.
——————————————————————————————————————
Message seen from the AP’s logs:
(317)IEEE802.1X auth is starting (at if=wifi0.2)
(318)Send message to RADIUS Server(192.168.60.166): code=1 (Access-Request) identifier=157 length=162, User-Name=domainusername NAS-IP-Address=192.168.10.10 Called-Station-Id=40-18-B1-F4-BB-15:Wireless-SSID Calling-Station-Id=C0-18-85-08-10-E1
(319)Receive message from RADIUS Server: code=11 (Access-Challenge) identifier=157 length=90
(320)Send message to RADIUS Server(192.168.60.166): code=1 (Access-Request) identifier=158 length=286, User-Name=domainusername NAS-IP-Address=192.168.10.10 Called-Station-Id=40-18-B1-F4-BB-15:Wireless-SSID Calling-Station-Id=C0-18-85-08-10-E1
(321)Send message to RADIUS Server(192.168.60.166): code=1 (Access-Request) identifier=161 length=162, User-Name=domainusername NAS-IP-Address=192.168.10.10 Called-Station-Id=40-18-B1-F4-BB-15:Wireless-SSID Calling-Station-Id=C0-18-85-08-10-E1
(322)Receive message from RADIUSServer: code=11 (Access-Challenge) identifier=161 length=90 BASIC
Output omitted
(330)Sta(at if=wifi0.2) is de-authenticated because of notification of driver
We have other NPS Servers with corresponding policy settings which are working so I am having trouble to understand why this errors occurs.
Initally the problem seemed to be related to the Cert on the NPS server cause it used the cert generated from the Somputer template. Now it uses the template for Domain controller just as the other NPS servers so this should not be the issue(Not sure if
this matters?)
Please guide me on how to take this further
Thank you 
//Cris
Contents
Introduction
This document examines common debugging problems for RADIUS when using Password Authentication Protocol (PAP) or Challenge Handshake Authentication Protocol (CHAP). Common PC settings for Microsoft Windows 95, Windows NT, Windows 98, and Windows 2000 are provided, as well as examples of configurations and examples of good and bad debugs.
Before You Begin
Conventions
For more information on document conventions, see the Cisco Technical Tips Conventions.
Prerequisites
There are no specific prerequisites for this document.
Components Used
The information in this document is based on Cisco IOS® Software Releases 11.2 and later.
The information presented in this document was created from devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If you are working in a live network, ensure that you understand the potential impact of any command before using it.
Common PC Setting
Windows 95
Follow the instructions provided below:
-
In the Dialup Networking window, select the connection name, then File > Properties.
-
On the Server Type tab, see if the Require Encrypted Password box beneath Type of Dial-up Server is checked.
-
If this box is checked, it means the PC accepts only CHAP authentication.
-
If this box is not checked, it means the PC accepts PAP or CHAP authentication.
-
Windows NT
Follow the instructions provided below:
-
In the Dial-Up Networking window, select the connection name, and then select File > Properties.
-
Check the settings on the Security tab:
-
If the Accept any authentication including clear text box is checked, this means the PC accepts PAP or CHAP.
-
If the Accept only encrypted authentication box is checked, the PC accepts only CHAP authentication.
-
Windows 98
Follow the instructions provided below:
-
In the Dial-Up Networking window, select the connection name, and then select Properties.
-
On the Server Types tab, check the settings in the Advanced Options area:
-
If the Require encrypted password box is unchecked, this means the PC accepts PAP or CHAP authentication.
-
If the Require encrypted password box is checked, this means the PC accepts only CHAP authentication.
-
Windows 2000
Follow the instructions provided below:
-
In Network and Dial-Up Connections, select the connection name, and then select Properties.
-
On the Security tab, check the settings in the Advanced > Settings > Allow these protocols area:
-
If the Unencrypted password (PAP) box is checked, the PC accepts PAP.
-
If the Challenge Handshake Authentication Protocol (CHAP) box is checked, the PC accepts CHAP per RFC 1994.
-
If the Microsoft CHAP (MS-CHAP) box is checked, the PC accepts MS-CHAP version 1 and does not accept CHAP per RFC 1994.
-
Configurations and Debug Examples
RADIUS and PAP
| Configuration — RADIUS and PAP |
|---|
Current configuration:
!
version 11.2
service timestamps debug uptime
no service password-encryption
service udp-small-servers
service tcp-small-servers
!
hostname rtpkrb
!
aaa new-model
!
!--- The following four command lines are specific to !--- Cisco IOS 11.2 and later, up until 11.3.3.T. !--- See below this configuration for commands !--- for other Cisco IOS releases.
!
aaa authentication login default radius local
aaa authentication ppp default if-needed radius local
aaa authorization exec radius if-authenticated
aaa authorization network radius if-authenticated
!
enable secret 5 $1$pkX.$JdAySRE1SbdbDe7bj0wyt0
enable password ww
!
username john password 0 doe
username cse password 0 csecse
ip host rtpkrb 10.31.1.5
ip domain-name RTP.CISCO.COM
ip name-server 171.68.118.103
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface Ethernet0
ip address 10.31.1.5 255.255.0.0
no mop enabled
!
interface Serial0
no ip address
no ip mroute-cache
shutdown
!
interface Serial1
no ip address
shutdown
!
interface Async1
ip unnumbered Ethernet0
encapsulation ppp
async mode dedicated
peer default ip address pool async
no cdp enable
ppp authentication pap
!
ip local pool async 15.15.15.15
ip classless
ip route 0.0.0.0 0.0.0.0 10.31.1.1
!
snmp-server community public RW
snmp-server host 171.68.118.100 traps public
radius-server host 171.68.118.101 auth-port 1645 acct-port 1646
radius-server key cisco
!
line con 0
line 1
session-timeout 20
exec-timeout 20 0
password ww
autoselect during-login
autoselect ppp
modem InOut
transport input all
stopbits 1
speed 38400
flowcontrol hardware
line 2
modem InOut
speed 38400
flowcontrol hardware
line 3 16
line aux 0
line vty 0 4
exec-timeout 0 0
password ww
!
end
|
Commands for Other Cisco IOS Releases
Note: To use these commands, remove the highlighted commands from the above configuration and paste these commands in, as dictated by your Cisco IOS release.
Cisco IOS 11.3.3.T until 12.0.5.T
aaa authen login default radius local aaa authen ppp default if-needed radius local aaa authorization exec default radius if-authenticated aaa authorization network default radius if-authenticated
Cisco IOS 12.0.5.T and Later
aaa authen login default group radius local aaa authen ppp default if-needed group radius local aaa authorization exec default group radius if-authenticated aaa authorization network default group radius if-authenticated
Sample Debugs — RADIUS and PAP
Note: In the debug output, the bold text highlights problems in the debug. Plain text indicates a good debug.
rtpkrb#
rtpkrb#sho deb
General OS:
AAA Authentication debugging is on
AAA Authorization debugging is on
PPP:
PPP authentication debugging is on
PPP protocol negotiation debugging is on
Radius protocol debugging is on
rtpkrb#
4d02h: As1 LCP: I CONFREQ [Closed] id 0 len 20
4d02h: As1 LCP: ACCM 0x00000000 (0x020600000000)
4d02h: As1 LCP: MagicNumber 0x00001F67 (0x050600001F67)
4d02h: As1 LCP: PFC (0x0702)
4d02h: As1 LCP: ACFC (0x0802)
4d02h: As1 LCP: Lower layer not up, discarding packet
%LINK-3-UPDOWN: Interface Async1, changed state to up
4d02h: As1 PPP: Treating connection as a dedicated line
4d02h: As1 PPP: Phase is ESTABLISHING, Active Open
4d02h: As1 LCP: O CONFREQ [Closed] id 85 len 24
4d02h: As1 LCP: ACCM 0x000A0000 (0x0206000A0000)
4d02h: As1 LCP: AuthProto PAP (0x0304C023)
4d02h: As1 LCP: MagicNumber 0xF54252D5 (0x0506F54252D5)
4d02h: As1 LCP: PFC (0x0702)
4d02h: As1 LCP: ACFC (0x0802)
PC insists on doing chap ('accept encrypted authentication only'),
but router is set up for pap:
As1 LCP: I CONFNAK [REQsent] id 98 len 12
As1 LCP: AuthProto 0xC123 (0x0308C12301000001)
As1 LCP: O CONFREQ [REQsent] id 99 len 24
As1 LCP: ACCM 0x000A0000 (0x0206000A0000)
As1 LCP: AuthProto PAP (0x0304C023)
As1 LCP: MagicNumber 0xF54D1AF8 (0x0506F54D1AF8)
As1 LCP: PFC (0x0702)
As1 LCP: ACFC (0x0802)
As1 LCP: I CONFREJ [REQsent] id 99 len 8
As1 LCP: AuthProto PAP (0x0304C023)
As1 PPP: Closing connection because remote won't authenticate
4d02h: As1 LCP: I CONFACK [REQsent] id 85 len 24
4d02h: As1 LCP: ACCM 0x000A0000 (0x0206000A0000)
4d02h: As1 LCP: AuthProto PAP (0x0304C023)
4d02h: As1 LCP: MagicNumber 0xF54252D5 (0x0506F54252D5)
4d02h: As1 LCP: PFC (0x0702)
4d02h: As1 LCP: ACFC (0x0802)
4d02h: As1 LCP: I CONFREQ [ACKrcvd] id 0 len 20
4d02h: As1 LCP: ACCM 0x00000000 (0x020600000000)
4d02h: As1 LCP: MagicNumber 0x00001F67 (0x050600001F67)
4d02h: As1 LCP: PFC (0x0702)
4d02h: As1 LCP: ACFC (0x0802)
4d02h: As1 LCP: O CONFACK [ACKrcvd] id 0 len 20
4d02h: As1 LCP: ACCM 0x00000000 (0x020600000000)
4d02h: As1 LCP: MagicNumber 0x00001F67 (0x050600001F67)
4d02h: As1 LCP: PFC (0x0702)
4d02h: As1 LCP: ACFC (0x0802)
4d02h: As1 LCP: State is Open
4d02h: As1 PPP: Phase is AUTHENTICATING, by this end
4d02h: As1 PAP: I AUTH-REQ id 14 len 19 from "ddunlap"
4d02h: As1 PAP: Authenticating peer ddunlap
4d02h: AAA/AUTHEN: create_user (0x15AD58) user='ddunlap' ruser=''
port='Async1' rem_addr='async' authen_type=PAP service=PPP priv=1
4d02h: AAA/AUTHEN/START (1953436918): port='Async1' list=''
action=LOGIN service=PPP
4d02h: AAA/AUTHEN/START (1953436918): using "default" list
4d02h: AAA/AUTHEN (1953436918): status = UNKNOWN
4d02h: AAA/AUTHEN/START (1953436918): Method=RADIUS
4d02h: RADIUS: Initial Transmit id 7 171.68.118.101:1645,
Access-Request, len 77
4d02h: Attribute 4 6 0A1F0105
4d02h: Attribute 5 6 00000001
4d02h: Attribute 61 6 00000000
4d02h: Attribute 1 9 6464756E
4d02h: Attribute 2 18 7882E0A5
4d02h: Attribute 6 6 00000002
4d02h: Attribute 7 6 00000001
Radius server is down - produces ERROR - since user is not
in local database, failover to local FAILs
As1 PAP: I AUTH-REQ id 16 len 19 from "ddunlap"
As1 AUTH: Duplicate authentication request id=16 already in progress
As1 PAP: I AUTH-REQ id 17 len 19 from "ddunlap"
As1 AUTH: Duplicate authentication request id=17 already in progress
RADIUS: Retransmit id 9
As1 PAP: I AUTH-REQ id 18 len 19 from "ddunlap"
As1 AUTH: Duplicate authentication request id=18 already in progress
As1 PAP: I AUTH-REQ id 19 len 19 from "ddunlap"
As1 AUTH: Duplicate authentication request id=19 already in progress
As1 PAP: I AUTH-REQ id 20 len 19 from "ddunlap"
As1 AUTH: Duplicate authentication request id=20 already in progress
RADIUS: Retransmit id 9
As1 PAP: I AUTH-REQ id 21 len 19 from "ddunlap"
As1 AUTH: Duplicate authentication request id=21 already in progress
As1 PAP: I AUTH-REQ id 22 len 19 from "ddunlap"
As1 AUTH: Duplicate authentication request id=22 already in progress
RADIUS: Retransmit id 9
As1 PAP: I AUTH-REQ id 23 len 19 from "ddunlap"
As1 AUTH: Duplicate authentication request id=23 already in progress
As1 LCP: I TERMREQ [Open] id 1 len 8 (0x000002CE)
As1 LCP: O TERMACK [Open] id 1 len 4
As1 PPP: Phase is TERMINATING
RADIUS: No response for id 9
%RADIUS-3-ALLDEADSERVER: No active radius servers found. Id 9.
RADIUS: No response from server
AAA/AUTHEN (3025998849): status = ERROR
AAA/AUTHEN/START (3025998849): Method=LOCAL
AAA/AUTHEN (3025998849): status = FAIL
Key in router does not match that of server:
RADIUS: Received from id 21 171.68.118.101:1645, Access-Reject, len 20
RADIUS: Reply for 21 fails decrypt
NT client sends 'DOMAINuser' and Radius server expects 'user':
RADIUS: Received from id 11 171.68.118.101:1645, Access-Reject, len 20
AAA/AUTHEN (1406749115): status = FAIL
As1 PAP: O AUTH-NAK id 25 len 32 msg is "Password validation failure"
As1 PPP: Phase is TERMINATING
As1 LCP: O TERMREQ [Open] id 108 len 4
AAA/AUTHEN: free_user (0xDA520) user='CISCOddunlap' ruser=''
port='Async1' rem_addr='async' authen_type=PAP service=PPP priv=1
Radius server refuses user because user user enters bad password,
or both userid & password are bad:
RADIUS: Received from id 12 171.68.118.101:1645, Access-Reject, len 20
AAA/AUTHEN (733718529): status = FAIL
As1 PAP: O AUTH-NAK id 26 len 32 msg is "Password validation failure"
As1 PPP: Phase is TERMINATING
As1 LCP: O TERMREQ [Open] id 111 len 4
AAA/AUTHEN: free_user (0x15B030) user='ddunlap' ruser=''
='Async1' rem_addr='async' authen_type=PAP service=PPP priv=1
User passes authentication (i.e. username/password is good)
but fails authorization (profile not set up for Service-Type=Framed &
Framed-Protocol=PPP):
RADIUS: Received from id 13 171.68.118.101:1645, Access-Accept, len 20
RADIUS: saved authorization data for user 15AD58 at 15ADF0
AAA/AUTHEN (56862281): status = PASS
AAA/AUTHOR/LCP As1: Authorize LCP
AAA/AUTHOR/LCP: Async1: (959162008): user='cse'
AAA/AUTHOR/LCP: Async1: (959162008): send AV service=ppp
AAA/AUTHOR/LCP: Async1: (959162008): send AV protocol=lcp
AAA/AUTHOR/LCP: Async1: (959162008): Method=RADIUS
RADIUS: no appropriate authorization type for user.
AAA/AUTHOR (959162008): Post authorization status = FAIL
AAA/AUTHOR/LCP As1: Denied
AAA/AUTHEN: free_user (0x15AD58) user='cse' ruser=''
port='Async1' rem_addr='async' authen_type=PAP service=PPP priv=1
As1 PAP: O AUTH-NAK id 27 len 25 msg is "Authorization failed"
4d02h: RADIUS: Received from id 7 171.68.118.101:1645, Access-Accept, len 32
4d02h: Attribute 6 6 00000002
4d02h: Attribute 7 6 00000001
4d02h: RADIUS: saved authorization data for user 15AD58 at 16C7F4
4d02h: AAA/AUTHEN (1953436918): status = PASS
4d02h: AAA/AUTHOR/LCP As1: Authorize LCP
4d02h: AAA/AUTHOR/LCP: Async1: (2587233868): user='ddunlap'
4d02h: AAA/AUTHOR/LCP: Async1: (2587233868): send AV service=ppp
4d02h: AAA/AUTHOR/LCP: Async1: (2587233868): send AV protocol=lcp
4d02h: AAA/AUTHOR/LCP: Async1: (2587233868): Method=RADIUS
4d02h: AAA/AUTHOR (2587233868): Post authorization status = PASS_REPL
4d02h: AAA/AUTHOR/LCP As1: Processing AV service=ppp
4d02h: As1 PAP: O AUTH-ACK id 14 len 5
4d02h: As1 PPP: Phase is UP
4d02h: AAA/AUTHOR/FSM As1: (0): Can we start IPCP?
4d02h: AAA/AUTHOR/FSM: Async1: (423372862): user='ddunlap'
4d02h: AAA/AUTHOR/FSM: Async1: (423372862): send AV service=ppp
4d02h: AAA/AUTHOR/FSM: Async1: (423372862): send AV protocol=ip
4d02h: AAA/AUTHOR/FSM: Async1: (423372862): Method=RADIUS
4d02h: AAA/AUTHOR (423372862): Post authorization status = PASS_REPL
4d02h: AAA/AUTHOR/FSM As1: We can start IPCP
4d02h: As1 IPCP: O CONFREQ [Closed] id 17 len 10
4d02h: As1 IPCP: Address 10.31.1.5 (0x03060A1F0105)
4d02h: As1 IPCP: I CONFREQ [REQsent] id 1 len 34
4d02h: As1 IPCP: Address 0.0.0.0 (0x030600000000)
4d02h: As1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000)
4d02h: As1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000)
4d02h: As1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000)
4d02h: As1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000)
4d02h: AAA/AUTHOR/IPCP As1: Start. Her address 0.0.0.0, we want 0.0.0.0
4d02h: AAA/AUTHOR/IPCP As1: Processing AV service=ppp
4d02h: AAA/AUTHOR/IPCP As1: Authorization succeeded
4d02h: AAA/AUTHOR/IPCP As1: Done. Her address 0.0.0.0, we want 0.0.0.0
4d02h: As1 IPCP: Using pool 'async'
4d02h: As1 IPCP: Pool returned 15.15.15.15
4d02h: As1 IPCP: O CONFREJ [REQsent] id 1 len 22
4d02h: As1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000)
4d02h: As1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000)
4d02h: As1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000)
4d02h: As1 IPCP: I CONFACK [REQsent] id 17 len 10
4d02h: As1 IPCP: Address 10.31.1.5 (0x03060A1F0105)
%LINEPROTO-5-UPDOWN: Line protocol on Interface Async1, changed state to up
4d02h: As1 IPCP: I CONFREQ [ACKrcvd] id 2 len 16
4d02h: As1 IPCP: Address 0.0.0.0 (0x030600000000)
4d02h: As1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000)
4d02h: AAA/AUTHOR/IPCP As1: Start. Her address 0.0.0.0, we want 15.15.15.15
4d02h: AAA/AUTHOR/IPCP As1: Processing AV service=ppp
4d02h: AAA/AUTHOR/IPCP As1: Authorization succeeded
4d02h: AAA/AUTHOR/IPCP As1: Done. Her address 0.0.0.0, we want 15.15.15.15
4d02h: As1 IPCP: O CONFNAK [ACKrcvd] id 2 len 16
4d02h: As1 IPCP: Address 15.15.15.15 (0x03060F0F0F0F)
4d02h: As1 IPCP: PrimaryDNS 171.68.118.103 (0x8106AB447667)
4d02h: As1 IPCP: I CONFREQ [ACKrcvd] id 3 len 16
4d02h: As1 IPCP: Address 15.15.15.15 (0x03060F0F0F0F)
4d02h: As1 IPCP: PrimaryDNS 171.68.118.103 (0x8106AB447667)
4d02h: AAA/AUTHOR/IPCP As1: Start. Her address 15.15.15.15, we want 15.15.15.15
4d02h: AAA/AUTHOR/IPCP: Async1: (4204275250): user='ddunlap'
4d02h: AAA/AUTHOR/IPCP: Async1: (4204275250): send AV service=ppp
4d02h: AAA/AUTHOR/IPCP: Async1: (4204275250): send AV protocol=ip
4d02h: AAA/AUTHOR/IPCP: Async1: (4204275250): send AV addr*15.15.15.15
4d02h: AAA/AUTHOR/IPCP: Async1: (4204275250): Method=RADIUS
4d02h: AAA/AUTHOR (4204275250): Post authorization status = PASS_REPL
4d02h: AAA/AUTHOR/IPCP As1: Reject 15.15.15.15, using 15.15.15.15
4d02h: AAA/AUTHOR/IPCP As1: Processing AV service=ppp
4d02h: AAA/AUTHOR/IPCP As1: Processing AV addr*15.15.15.15
4d02h: AAA/AUTHOR/IPCP As1: Authorization succeeded
4d02h: AAA/AUTHOR/IPCP As1: Done. Her address 15.15.15.15, we want 15.15.15.15
4d02h: As1 IPCP: O CONFACK [ACKrcvd] id 3 len 16
4d02h: As1 IPCP: Address 15.15.15.15 (0x03060F0F0F0F)
4d02h: As1 IPCP: PrimaryDNS 171.68.118.103 (0x8106AB447667)
4d02h: As1 IPCP: State is Open
4d02h: As1 IPCP: Install route to 15.15.15.15
rtpkrb#
RADIUS and CHAP
| Configuration — RADIUS and CHAP |
|---|
Current configuration:
!
version 11.2
service timestamps debug uptime
no service password-encryption
service udp-small-servers
service tcp-small-servers
!
hostname rtpkrb
!
aaa new-model
!
!--- The following four command lines are specific to !--- Cisco IOS 11.2 and later, up until 11.3.3.T. !--- See below this configuration for commands !--- for other Cisco IOS releases.
!
aaa authentication login default radius local
aaa authentication ppp default if-needed radius local
aaa authorization exec radius if-authenticated
aaa authorization network radius if-authenticated
!
enable secret 5 $1$pkX.$JdAySRE1SbdbDe7bj0wyt0
enable password ww
!
username john password 0 doe
username cse password 0 csecse
ip host rtpkrb 10.31.1.5
ip name-server 171.68.118.103
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface Ethernet0
ip address 10.31.1.5 255.255.0.0
no mop enabled
!
interface Serial0
no ip address
no ip mroute-cache
shutdown
!
interface Serial1
no ip address
shutdown
!
interface Async1
ip unnumbered Ethernet0
encapsulation ppp
async mode dedicated
peer default ip address pool async
no cdp enable
ppp authentication chap
!
ip local pool async 15.15.15.15
ip classless
ip route 0.0.0.0 0.0.0.0 10.31.1.1
!
snmp-server community public RW
snmp-server host 171.68.118.100 traps public
radius-server host 171.68.118.101 auth-port 1645 acct-port 1646
radius-server key cisco
!
line con 0
line 1
session-timeout 20
exec-timeout 20 0
password ww
autoselect during-login
autoselect ppp
modem InOut
transport input all
stopbits 1
speed 38400
flowcontrol hardware
line 2
modem InOut
speed 38400
flowcontrol hardware
line 3 16
line aux 0
line vty 0 4
exec-timeout 0 0
password ww
!
end
|
Commands for Other Cisco IOS Releases
Note: To use these commands, remove the highlighted commands from the above configuration and paste these commands in, as dictated by your Cisco IOS release.
Cisco IOS 11.3.3.T until 12.0.5.T
aaa authen login default radius local aaa authen ppp default if-needed radius local aaa authorization exec default radius if-authenticated aaa authorization network default radius if-authenticated
Cisco IOS 12.0.5.T and Later
aaa authen login default group radius local aaa authen ppp default if-needed group radius local aaa authorization exec default group radius if-authenticated aaa authorization network default group radius if-authenticated
Sample Debugs — RADIUS and CHAP
Note: In the debug output, the bold, italicized text highlights problems in the debug. Plain text indicates a good debug.
rtpkrb#show debug General OS: AAA Authentication debugging is on AAA Authorization debugging is on PPP: PPP authentication debugging is on PPP protocol negotiation debugging is on Radius protocol debugging is on rtpkrb# 4d02h: As1 LCP: I CONFREQ [Closed] id 0 len 20 4d02h: As1 LCP: ACCM 0x00000000 (0x020600000000) 4d02h: As1 LCP: MagicNumber 0x0000405F (0x05060000405F) 4d02h: As1 LCP: PFC (0x0702) 4d02h: As1 LCP: ACFC (0x0802) 4d02h: As1 LCP: Lower layer not up, discarding packet %LINK-3-UPDOWN: Interface Async1, changed state to up 4d02h: As1 PPP: Treating connection as a dedicated line 4d02h: As1 PPP: Phase is ESTABLISHING, Active Open 4d02h: As1 LCP: O CONFREQ [Closed] id 87 len 25 4d02h: As1 LCP: ACCM 0x000A0000 (0x0206000A0000) 4d02h: As1 LCP: AuthProto CHAP (0x0305C22305) 4d02h: As1 LCP: MagicNumber 0xF5445B55 (0x0506F5445B55) 4d02h: As1 LCP: PFC (0x0702) 4d02h: As1 LCP: ACFC (0x0802) 4d02h: As1 LCP: I CONFACK [REQsent] id 87 len 25 4d02h: As1 LCP: ACCM 0x000A0000 (0x0206000A0000) 4d02h: As1 LCP: AuthProto CHAP (0x0305C22305) 4d02h: As1 LCP: MagicNumber 0xF5445B55 (0x0506F5445B55) 4d02h: As1 LCP: PFC (0x0702) 4d02h: As1 LCP: ACFC (0x0802) 4d02h: As1 LCP: I CONFREQ [ACKrcvd] id 0 len 20 4d02h: As1 LCP: ACCM 0x00000000 (0x020600000000) 4d02h: As1 LCP: MagicNumber 0x0000405F (0x05060000405F) 4d02h: As1 LCP: PFC (0x0702) 4d02h: As1 LCP: ACFC (0x0802) 4d02h: As1 LCP: O CONFACK [ACKrcvd] id 0 len 20 4d02h: As1 LCP: ACCM 0x00000000 (0x020600000000) 4d02h: As1 LCP: MagicNumber 0x0000405F (0x05060000405F) 4d02h: As1 LCP: PFC (0x0702) 4d02h: As1 LCP: ACFC (0x0802) 4d02h: As1 LCP: State is Open 4d02h: As1 PPP: Phase is AUTHENTICATING, by this end 4d02h: As1 CHAP: O CHALLENGE id 11 len 27 from "rtpkrb" 4d02h: As1 CHAP: I RESPONSE id 11 len 28 from "chapadd" 4d02h: AAA/AUTHEN: create_user (0x15AD58) user='chapadd' ruser='' port='Async1' rem_addr='async' authen_type=CHAP service=PPP priv=1 4d02h: AAA/AUTHEN/START (575703226): port='Async1' list='' action=LOGIN service=PPP 4d02h: AAA/AUTHEN/START (575703226): using "default" list 4d02h: AAA/AUTHEN (575703226): status = UNKNOWN 4d02h: AAA/AUTHEN/START (575703226): Method=RADIUS 4d02h: RADIUS: Initial Transmit id 8 171.68.118.101:1645, Access-Request, len 78 4d02h: Attribute 4 6 0A1F0105 4d02h: Attribute 5 6 00000001 4d02h: Attribute 61 6 00000000 4d02h: Attribute 1 9 63686170 4d02h: Attribute 3 19 0B895D57 4d02h: Attribute 6 6 00000002 4d02h: Attribute 7 6 00000001 Radius server is down - produces ERROR - since user is not in local database, failover to local FAILs: As1 CHAP: I RESPONSE id 12 len 28 from "chapadd" As1 AUTH: Duplicate authentication request id=12 already in progress As1 CHAP: I RESPONSE id 12 len 28 from "chapadd" As1 AUTH: Duplicate authentication request id=12 already in progress RADIUS: Retransmit id 15 As1 CHAP: I RESPONSE id 12 len 28 from "chapadd" As1 AUTH: Duplicate authentication request id=12 already in progress As1 CHAP: I RESPONSE id 12 len 28 from "chapadd" As1 AUTH: Duplicate authentication request id=12 already in progress As1 CHAP: I RESPONSE id 12 len 28 from "chapadd" As1 AUTH: Duplicate authentication request id=12 already in progress RADIUS: Retransmit id 15 As1 CHAP: I RESPONSE id 12 len 28 from "chapadd" As1 AUTH: Duplicate authentication request id=12 already in progress As1 CHAP: I RESPONSE id 12 len 28 from "chapadd" As1 AUTH: Duplicate authentication request id=12 already in progress RADIUS: Retransmit id 15 As1 CHAP: I RESPONSE id 12 len 28 from "chapadd" As1 AUTH: Duplicate authentication request id=12 already in progress As1 LCP: I TERMREQ [Open] id 1 len 8 (0x000002CE) As1 LCP: O TERMACK [Open] id 1 len 4 As1 PPP: Phase is TERMINATING RADIUS: id 15, requester hung up. RADIUS: No response for id 15 RADIUS: No response from server AAA/AUTHEN (1866705040): status = ERROR AAA/AUTHEN/START (1866705040): Method=LOCAL AAA/AUTHEN (1866705040): status = FAIL As1 CHAP: Unable to validate Response. Username chapadd: Authentication failure As1 CHAP: O FAILURE id 12 len 26 msg is "Authentication failure" AAA/AUTHEN: free_user (0x1716B8) user='chapadd' ruser='' port='Async1' rem_addr='async' authen_type=CHAP service=PPP priv=1 Key in router does not match that of server: RADIUS: Received from id 21 171.68.118.101:1645, Access-Reject, len 20 RADIUS: Reply for 21 fails decrypt NT client sends 'DOMAINuser' and Radius server expects 'user': RADIUS: Received from id 16 171.68.118.101:1645, Access-Reject, len 20 AAA/AUTHEN (2974782384): status = FAIL As1 CHAP: Unable to validate Response. Username CISCOchapadd: Authentication failure As1 CHAP: O FAILURE id 13 len 26 msg is "Authentication failure" As1 PPP: Phase is TERMINATING As1 LCP: O TERMREQ [Open] id 131 len 4 AAA/AUTHEN: free_user (0x171700) user='CISCOchapadd' ruser='' port='Async1' rem_addr='async' authen_type=CHAP service=PPP priv=1 Radius server refuses user because user is set up for pap, user enters bad password, or both userid & password are bad: RADIUS: Received from id 17 171.68.118.101:1645, Access-Reject, len 20 AAA/AUTHEN (3898168391): status = FAIL As1 CHAP: Unable to validate Response. Username ddunlap: Authentication failure As1 CHAP: O FAILURE id 14 len 26 msg is "Authentication failure" As1 PPP: Phase is TERMINATING As1 LCP: O TERMREQ [Open] id 134 len 4 AAA/AUTHEN: free_user (0x1716B8) user='ddunlap' ruser='' port='Async1' rem_addr='async' authen_type=CHAP service=PPP priv=1 User PASSes authentication (i.e. username/password is good) but FAILs authorization (profile not set up for Service-Type=Framed & Framed-Protocol=PPP): RADIUS: Received from id 19 171.68.118.101:1645, Access-Accept, len 20 AAA/AUTHEN (2006894701): status = PASS AAA/AUTHOR/LCP As1: Authorize LCP AAA/AUTHOR/LCP: Async1: (2370106832): user='noauth' AAA/AUTHOR/LCP: Async1: (2370106832): send AV service=ppp AAA/AUTHOR/LCP: Async1: (2370106832): send AV protocol=lcp AAA/AUTHOR/LCP: Async1: (2370106832): Method=RADIUS RADIUS: no appropriate authorization type for user. AAA/AUTHOR (2370106832): Post authorization status = FAIL AAA/AUTHOR/LCP As1: Denied 4d02h: RADIUS: Received from id 8 171.68.118.101:1645, Access-Accept, len 32 4d02h: Attribute 6 6 00000002 4d02h: Attribute 7 6 00000001 4d02h: AAA/AUTHEN (575703226): status = PASS 4d02h: AAA/AUTHOR/LCP As1: Authorize LCP 4d02h: AAA/AUTHOR/LCP: Async1: (4143416222): user='chapadd' 4d02h: AAA/AUTHOR/LCP: Async1: (4143416222): send AV service=ppp 4d02h: AAA/AUTHOR/LCP: Async1: (4143416222): send AV protocol=lcp 4d02h: AAA/AUTHOR/LCP: Async1: (4143416222): Method=RADIUS 4d02h: AAA/AUTHOR (4143416222): Post authorization status = PASS_REPL 4d02h: AAA/AUTHOR/LCP As1: Processing AV service=ppp 4d02h: As1 CHAP: O SUCCESS id 11 len 4 4d02h: As1 PPP: Phase is UP 4d02h: AAA/AUTHOR/FSM As1: (0): Can we start IPCP? 4d02h: AAA/AUTHOR/FSM: Async1: (1916451991): user='chapadd' 4d02h: AAA/AUTHOR/FSM: Async1: (1916451991): send AV service=ppp 4d02h: AAA/AUTHOR/FSM: Async1: (1916451991): send AV protocol=ip 4d02h: AAA/AUTHOR/FSM: Async1: (1916451991): Method=RADIUS 4d02h: AAA/AUTHOR (1916451991): Post authorization status = PASS_REPL 4d02h: AAA/AUTHOR/FSM As1: We can start IPCP 4d02h: As1 IPCP: O CONFREQ [Closed] id 19 len 10 4d02h: As1 IPCP: Address 10.31.1.5 (0x03060A1F0105) 4d02h: As1 IPCP: I CONFREQ [REQsent] id 1 len 34 4d02h: As1 IPCP: Address 0.0.0.0 (0x030600000000) 4d02h: As1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000) 4d02h: As1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000) 4d02h: As1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000) 4d02h: As1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000) 4d02h: AAA/AUTHOR/IPCP As1: Start. Her address 0.0.0.0, we want 0.0.0.0 4d02h: AAA/AUTHOR/IPCP As1: Processing AV service=ppp 4d02h: AAA/AUTHOR/IPCP As1: Authorization succeeded 4d02h: AAA/AUTHOR/IPCP As1: Done. Her address 0.0.0.0, we want 0.0.0.0 4d02h: As1 IPCP: Using pool 'async' 4d02h: As1 IPCP: Pool returned 15.15.15.15 4d02h: As1 IPCP: O CONFREJ [REQsent] id 1 len 22 4d02h: As1 IPCP: PrimaryWINS 0.0.0.0 (0x820600000000) 4d02h: As1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000) 4d02h: As1 IPCP: SecondaryWINS 0.0.0.0 (0x840600000000) 4d02h: As1 IPCP: I CONFACK [REQsent] id 19 len 10 4d02h: As1 IPCP: Address 10.31.1.5 (0x03060A1F0105) 4d02h: As1 IPCP: I CONFREQ [ACKrcvd] id 2 len 16 4d02h: As1 IPCP: Address 0.0.0.0 (0x030600000000) 4d02h: As1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000) 4d02h: AAA/AUTHOR/IPCP As1: Start. Her address 0.0.0.0, we want 15.15.15.15 4d02h: AAA/AUTHOR/IPCP As1: Processing AV service=ppp 4d02h: AAA/AUTHOR/IPCP As1: Authorization succeeded 4d02h: AAA/AUTHOR/IPCP As1: Done. Her address 0.0.0.0, we want 15.15.15.15 4d02h: As1 IPCP: O CONFNAK [ACKrcvd] id 2 len 16 4d02h: As1 IPCP: Address 15.15.15.15 (0x03060F0F0F0F) 4d02h: As1 IPCP: PrimaryDNS 171.68.118.103 (0x8106AB447667) 4d02h: As1 IPCP: I CONFREQ [ACKrcvd] id 3 len 16 4d02h: As1 IPCP: Address 15.15.15.15 (0x03060F0F0F0F) 4d02h: As1 IPCP: PrimaryDNS 171.68.118.103 (0x8106AB447667) 4d02h: AAA/AUTHOR/IPCP As1: Start. Her address 15.15.15.15, we want 15.15.15.15 4d02h: AAA/AUTHOR/IPCP: Async1: (1096193147): user='chapadd' 4d02h: AAA/AUTHOR/IPCP: Async1: (1096193147): send AV service=ppp 4d02h: AAA/AUTHOR/IPCP: Async1: (1096193147): send AV protocol=ip 4d02h: AAA/AUTHOR/IPCP: Async1: (1096193147): send AV addr*15.15.15.15 4d02h: AAA/AUTHOR/IPCP: Async1: (1096193147): Method=RADIUS 4d02h: AAA/AUTHOR (1096193147): Post authorization status = PASS_REPL 4d02h: AAA/AUTHOR/IPCP As1: Reject 15.15.15.15, using 15.15.15.15 4d02h: AAA/AUTHOR/IPCP As1: Processing AV service=ppp 4d02h: AAA/AUTHOR/IPCP As1: Processing AV addr*15.15.15.15 4d02h: AAA/AUTHOR/IPCP As1: Authorization succeeded 4d02h: AAA/AUTHOR/IPCP As1: Done. Her address 15.15.15.15, we want 15.15.15.15 4d02h: As1 IPCP: O CONFACK [ACKrcvd] id 3 len 16 4d02h: As1 IPCP: Address 15.15.15.15 (0x03060F0F0F0F) 4d02h: As1 IPCP: PrimaryDNS 171.68.118.103 (0x8106AB447667) 4d02h: As1 IPCP: State is Open %LINEPROTO-5-UPDOWN: Line protocol on Interface Async1, changed state to up 4d02h: As1 IPCP: Install route to 15.15.15.15 rtpkrb#
Debug Commands
The following debug commands were used to produce the sample debug output in this document.
Note: Before issuing debug commands, please see Important Information on Debug Commands.
-
debug aaa authentication — Display information on AAA authentication.
-
debug aaa authorization — Display information on AAA authorization.
-
debug radius — Display detailed debugging information associated with the Remote Authentication Dial-In User Server (RADIUS).
-
debug ppp negotiation — Displays PPP packets transmitted during PPP startup, where PPP options are negotiated.
Related Information
- RADIUS Support Page
- Technical Support — Cisco Systems