Содержание
- RPCS3 crashes at startup (win 7) #10271
- Comments
- [Fixed]Unrecognizable error when loading game #2753
- Comments
- Fatal error
- HOW TO REPORT ERRORS: Check the FAQ, README, other sources. Please, don’t send incorrect reports. Thanks for understanding. Press (Ctrl+C) to copy this message.
- Segfault on «Install Firmware» on Linux #3908
- Comments
- Rpcs3 fatal error segfault
- wiepout hd/fury rsx thread crash about rpcs3 HOT 19 CLOSED
- Comments (19)
- Related Issues (20)
- Recommend Projects
- React
- Vue.js
- Typescript
- TensorFlow
- Django
- Laravel
- Recommend Topics
- javascript
- server
- Machine learning
- Visualization
- Recommend Org
- Microsoft
RPCS3 crashes at startup (win 7) #10271
Continue #10243 for win7
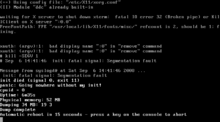
Unhandled Win32 exception 0xC0000005.
Segfault writing location 0000000000000000 at 000007fefcf7c4d2.
Thread: Main Thread.
Instruction address: 000007fefcf7c4d2.
Function address: 000007fefcf7c410 (base+0xc410).
Module name: ‘KERNELBASE.dll’.
Module base: 000007fefcf70000.
RPCS3 image base: 0000000000010000.
Thread id = 22568.
Test on latest 12240
OS win7+all updates
all NTFS disk
The text was updated successfully, but these errors were encountered:
I’ll check what can be done to workaround it. I think it’s win 7 bug with memory mapping big sparse files, but can’t say for sure.
I’m having this EXACT same problem. Old version works fine (at least it opens) but with the last one I get this same error.
Backtrace could be helpful, can’t tell where it’s coming from.
Does the below help?
Reported fixed, feel free to reopen if the issue is not fixed.
I still have this problem on windows 7
Built and debugged a little and it looks like DeviceIoControl is incorrectly called with lpBytesReturned set to null
if ((info0. FileAttributes & FILE_ATTRIBUTE_SPARSE_FILE) || DeviceIoControl (h, FSCTL_SET_SPARSE, &arg, sizeof (arg), nullptr , 0 , nullptr , nullptr ))
passing variable fix issue for me but I dont understand how it works for anyone because per DeviceIoControl docs:
If lpOverlapped is NULL, lpBytesReturned cannot be NULL. Even when an operation returns no output data and lpOutBuffer is NULL, DeviceIoControl makes use of lpBytesReturned. After such an operation, the value of lpBytesReturned is meaningless.
and that’s why we get null pointer exception
I guess win 10 don’t care about documentation
Источник
[Fixed]Unrecognizable error when loading game #2753
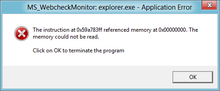
EDIT: OK, so because I had no audio device, both xaudio and openAL made the game crash. fixed by setting it to null.
Hi! When I Try to load persona 5, I get this error:
Fatal error
Unhandled Win32 exception 0xC0000005.
Segfault reading location 000000000f0e0090 at 000000000106e046.
Instruction address: 000000000106e046.
Function address: 000000000106df70 (base+0x105df70).
Module name: ‘rpcs3.exe’.
Module base: 0000000000010000.
RPCS3 image base: 0000000000010000.
HOW TO REPORT ERRORS: Check the FAQ, README, other sources.
Please, don’t send incorrect reports. Thanks for understanding.
Press (Ctrl+C) to copy this message.
I looked up the unhandled Win 32 exception issue and this is what I found on Microsoft support: This issue occurs because of a race condition. When a thread tries to close the handle to an object that is being destroyed, the operation fails.
And I have a Quardo K22000. Could you guys tell me what’s going on? Thanks!
EDIT: Added log file plus added config info and tried with both both Interpreters (fast) and 1280×720 with openGL.
could it be because i’m not using it in administrator mode?
The text was updated successfully, but these errors were encountered:
Источник
Segfault on «Install Firmware» on Linux #3908
I just downloaded the last build of RPCS3 ( rpcs3-v0.0.4-2017-12-06-0b3fbf1-9095_linux64.AppImage ), I followed the Quickstart Guide to install firmware, but when I click on «File > Install firmware» I have a fatal error saying:
Segfault reading location 0000000000000000 at 00007f5e04f502c7.
I kept the default configuration of RPCS3, here is my computer configuration:
Please let me know if you need more information for this issue!
EDIT: I launched rpcs3 from command line using admin privileges «sudo ./rpcs. «, and eveyrthing worked! But I this shouldn’t happen as a common user, for now I close this issue, if I find something about this issue I’ll open another one
The text was updated successfully, but these errors were encountered:
woah, please re-open this, you should NEVER need to run rpcs3 via sudo.
Here is some update:
Running it with sudo removes the segfault when installing a pkg or firmware
But when playing (Alice: Madness returns, this is the one I tried) I have back the segfault on the exact same address even when running as sudo
I’m gonna tag @probonopd because the issue has to do with AppImages, and hopefully he knows of some solutions.
I was able to reproduce this in Pop! OS in virtualbox, and I’d assume it would also repro in Ubuntu 17.10.
The issue I’m seeing has something to do with libglib, when gtk3 is trying to open a file. Is this something we can bundle with the AppImage?
I just checked and it’s running on x11, so it’s not an issue with wayland.
Источник
Rpcs3 fatal error segfault
Ani
Administrator
You don’t download DLLs from shady google websites. Delete the whole folder and start again.
You’re missing Visual Studio C++ 2015 Redis. dependency. If you happen to have it, uninstall it then install http://www.microsoft.com/en-us/download/. x?id=48145
(02-07-2017, 02:26 PM) Annie Wrote: You’re missing Visual Studio C++ 2015 Redis. dependency. If you happen to have it, uninstall it then install http://www.microsoft.com/en-us/download/. x?id=48145
Also, I’d recommend reading https://rpcs3.net/quickstart
Thank you very much for such insight! As it turned out, I really was completely missing this Visual Studio C++ 2015 thing in my system. As soon as I installed that application from your link and reinstalled the RPCS3 then I was finally able to load a blank window of the emulator and browse through the menus.
But now when I followed the instructions of the Quickstart guide and tried to boot a game after copying it into an ID folder, I got the following error message:
—————————
Fatal error
—————————
Unhandled Win32 exception 0xC0000005.
Segfault writing location 0000000000000000 at 0000000000000000.
Instruction address: 0000000000000000.
RPCS3 image base: 0000000000010000.
So now I am wondering: How can I fix this new error? And what does this new error mean?
ssshadow
Administrator
Источник
wiepout hd/fury rsx thread crash about rpcs3 HOT 19 CLOSED
Try setting FIFO accuracy to atomic in the advanced tab. And enable accurate RSX reservations as well.
This combination eliminates like 90% of all desyncs.
zelurker commented on January 16, 2023
Try setting FIFO accuracy to atomic in the advanced tab. And enable accurate RSX reservations as well. This combination eliminates like 90% of all desyncs.
Thanks for the tip, I didn’t know this option, but sadly it crashed again in the 3rd lap of vineta k, venom, with the ikaras.
It just gave me time to improve my time in the 2nd lap ! 😉
The message this time :
RPCS3: RSX [0x0075130]: SIG: Thread terminated due to fatal error: Segfault reading location 00000008038822ec at 0000000000c790e4.
Emu Thread Name: ‘rsx::thread’.
corrupted size vs. prev_size while consolidating
and core dump
kd-11 commented on January 16, 2023
Hmm, that’s worrying, but I’ve seen it before on linux. I’ll have to investigate.
solarmystic commented on January 16, 2023
Definitely seems to be Linux specific. I’ve just gone through the Vineta k multiple times on Windows now using 0.0.24-14175 during a Tournament run, and it was perfect with no Fatal Errors.
kd-11 commented on January 16, 2023
I see you have the debug setting «Use GPU texture scaling» enabled. Please disable that. I’ll also make some code changes to remove it, it’s not meant to be used outside dev stuff.
zelurker commented on January 16, 2023
I see you have the debug setting «Use GPU texture scaling» enabled. Please disable that. I’ll also make some code changes to remove it, it’s not meant to be used outside dev stuff.
I could not find this setting anywhere in the gui, so I edited directly the custom config file to set it to false. I don’t remember how it could be set to true. !
After that I could do 5 laps with the feisar, then switched to the Ikaras and it crashed on start ! Thanks for your investigation anyway !
AniLeo commented on January 16, 2023
Missing build where it regressed
zelurker commented on January 16, 2023
YuriNator557 commented on January 16, 2023
The regression must be found if you want it fixing, even if it takes a long time
kd-11 commented on January 16, 2023
I’ve removed the regression in the title. It is mentioned in the OP’s description that it already used to happen. Frequency doesn’t matter — the bug either exists or it doesn’t.
Unfortunately I am unable to reproduce this issue even after leaving the game running for an extended amount of time. Grabbing a debug log requires a full dev environment for this kind of bug as well especially on linux where the affected system would need a proper local build with debug symbols present in the binary, something we don’t have with appimages.
zelurker commented on January 16, 2023
zelurker commented on January 16, 2023
kd-11 commented on January 16, 2023
I’ll push a debug branch somewhere to get more information and some stacktraces.
zelurker commented on January 16, 2023
zelurker commented on January 16, 2023
zelurker commented on January 16, 2023
tr1p0p commented on January 16, 2023
I have this too, on linux fedora last appimage relase
italoghost commented on January 16, 2023
I have the same segfault as @zelurker but on The Last Of Us:
·F 0:02:18.330845 SIG: Thread terminated due to fatal error: Segfault reading location 0000000803a98a74 at 0000000000d4b79b.
Emu Thread Name: ‘rsx::thread’.
Arch Linux Gnome 42 Wayland
Using both the rpcs3-git (0.0.24-14203-8170b91f Alpha) and the AppImage (latest).
kd-11 commented on January 16, 2023
- NCAA 14 keeps crashing after it reaches the start menu HOT 1
- #KILLALLZOMBIES crashes after launching HOT 2
- [Regression] Multithreaded package installation is broken
- [Feature request] Optional atomic PKGs install
- Debug build on Linux HOT 2
- M1 Mac — Unable to connect Lego Dimension Portal
- [Regression] (VSH) Building database crash (#13115) HOT 6
- Installing a PKG file that overwrites lower case files with upper case files does not work. HOT 4
- Call of Duty 3 [BLES00016] — Invisible trees
- [Feature Request] Proper Image Provider
- Fatal Error when using Gamestream Launchpad HOT 6
- Support for non-sony PS4 controllers on Mac — wireless / bluetooth pads HOT 1
- [Feature request] Inform the guest application that the disc has been ejected if the file path becomes inaccessible. HOT 4
- Fracture Graphical Issues
- Pro Evolution Soccer Graphical issues
- Issues with RSX capture
- NHL 09 Graphical Issue
- Trinity Souls of Zill O’ll Graphical Issue (Nivida 30 series) HOT 2
- Deadstorm Pirates sound issues HOT 1
- Freeze Skyalnders Giants
Recommend Projects
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
TensorFlow
An Open Source Machine Learning Framework for Everyone
Django
The Web framework for perfectionists with deadlines.
Laravel
A PHP framework for web artisans
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
Recommend Topics
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
Some thing interesting about web. New door for the world.
server
A server is a program made to process requests and deliver data to clients.
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
Visualization
Some thing interesting about visualization, use data art
Some thing interesting about game, make everyone happy.
Recommend Org
We are working to build community through open source technology. NB: members must have two-factor auth.
Microsoft
Open source projects and samples from Microsoft.
Источник
What is the root cause of the segmentation fault (SIGSEGV), and how to handle it?
Rohan Bari
7,3843 gold badges13 silver badges34 bronze badges
asked Oct 14, 2009 at 5:20
0
Wikipedia has the answer, along with a number of other sources.
A segfault basically means you did something bad with pointers. This is probably a segfault:
char *c = NULL;
...
*c; // dereferencing a NULL pointer
Or this:
char *c = "Hello";
...
c[10] = 'z'; // out of bounds, or in this case, writing into read-only memory
Or maybe this:
char *c = new char[10];
...
delete [] c;
...
c[2] = 'z'; // accessing freed memory
Same basic principle in each case — you’re doing something with memory that isn’t yours.
answered Oct 14, 2009 at 5:25
Chris LutzChris Lutz
72.2k16 gold badges128 silver badges182 bronze badges
There are various causes of segmentation faults, but fundamentally, you are accessing memory incorrectly. This could be caused by dereferencing a null pointer, or by trying to modify readonly memory, or by using a pointer to somewhere that is not mapped into the memory space of your process (that probably means you are trying to use a number as a pointer, or you incremented a pointer too far). On some machines, it is possible for a misaligned access via a pointer to cause the problem too — if you have an odd address and try to read an even number of bytes from it, for example (that can generate SIGBUS, instead).
answered Oct 14, 2009 at 5:25
Jonathan LefflerJonathan Leffler
718k138 gold badges893 silver badges1260 bronze badges
2
using an invalid/null pointer? Overrunning the bounds of an array? Kindof hard to be specific without any sample code.
Essentially, you are attempting to access memory that doesn’t belong to your program, so the OS kills it.
answered Oct 14, 2009 at 5:22
MichaelMMichaelM
5,2782 gold badges29 silver badges23 bronze badges
Here is an example of SIGSEGV.
root@pierr-desktop:/opt/playGround# cat test.c
int main()
{
int * p ;
* p = 0x1234;
return 0 ;
}
root@pierr-desktop:/opt/playGround# g++ -o test test.c
root@pierr-desktop:/opt/playGround# ./test
Segmentation fault
And here is the detail.
How to handle it?
-
Avoid it as much as possible in the
first place.Program defensively: use assert(), check for NULL pointer , check for buffer overflow.
Use static analysis tools to examine your code.
compile your code with -Werror -Wall.
Has somebody review your code.
-
When that actually happened.
Examine you code carefully.
Check what you have changed since the last time you code run successfully without crash.
Hopefully, gdb will give you a call stack so that you know where the crash happened.
EDIT : sorry for a rush. It should be *p = 0x1234; instead of p = 0x1234;
answered Oct 14, 2009 at 5:23
pierrotlefoupierrotlefou
39.1k35 gold badges134 silver badges174 bronze badges
4
SigSegV means a signal for memory access violation, trying to read or write from/to a memory area that your process does not have access to. These are not C or C++ exceptions and you can’t catch signals. It’s possible indeed to write a signal handler that ignores the problem and allows continued execution of your unstable program in undefined state, but it should be obvious that this is a very bad idea.
Most of the time this is because of a bug in the program. The memory address given can help debug what’s the problem (if it’s close to zero then it’s likely a null pointer dereference, if the address is something like 0xadcedfe then it’s intentional safeguard or a debug check, etc.)
One way of “catching” the signal is to run your stuff in a separate child process that can then abruptly terminate without taking your main process down with it. Finding the root cause and fixing it is obviously preferred over workarounds like this.
answered May 23, 2019 at 15:05
The initial source cause can also be an out of memory.
answered Nov 13, 2020 at 16:07
MakusensuMakusensu
2793 silver badges10 bronze badges
2
Segmentation fault arrives when you access memory which is not declared by the program. You can do this through pointers i.e through memory addresses. Or this may also be due to stackoverflow for example:
void rec_func() {int q = 5; rec_func();}
int main() {rec_func();}
This call will keep on consuming stack memory until it’s completely filled and thus finally stackoverflow happens.
Note: it might not be visible in some competitive questions as it leads to timeouterror first but for those in which timeout doesn’t happens its a hard time figuring out SIGSEGV.
answered Oct 14, 2018 at 7:03
From Wikipedia, the free encyclopedia
In computing, a segmentation fault (often shortened to segfault) or access violation is a fault, or failure condition, raised by hardware with memory protection, notifying an operating system (OS) the software has attempted to access a restricted area of memory (a memory access violation). On standard x86 computers, this is a form of general protection fault. The operating system kernel will, in response, usually perform some corrective action, generally passing the fault on to the offending process by sending the process a signal. Processes can in some cases install a custom signal handler, allowing them to recover on their own,[1] but otherwise the OS default signal handler is used, generally causing abnormal termination of the process (a program crash), and sometimes a core dump.
Segmentation faults are a common class of error in programs written in languages like C that provide low-level memory access and few to no safety checks. They arise primarily due to errors in use of pointers for virtual memory addressing, particularly illegal access. Another type of memory access error is a bus error, which also has various causes, but is today much rarer; these occur primarily due to incorrect physical memory addressing, or due to misaligned memory access – these are memory references that the hardware cannot address, rather than references that a process is not allowed to address.
Many programming languages may employ mechanisms designed to avoid segmentation faults and improve memory safety. For example, Rust employs an ownership-based[2] model to ensure memory safety.[3] Other languages, such as Lisp and Java, employ garbage collection,[4] which avoids certain classes of memory errors that could lead to segmentation faults.[5]
Overview[edit]
Example of human generated signal
Segmentation fault affecting Krita in KDE desktop environment
A segmentation fault occurs when a program attempts to access a memory location that it is not allowed to access, or attempts to access a memory location in a way that is not allowed (for example, attempting to write to a read-only location, or to overwrite part of the operating system).
The term «segmentation» has various uses in computing; in the context of «segmentation fault», a term used since the 1950s,[citation needed] it refers to the address space of a program.[6] With memory protection, only the program’s own address space is readable, and of this, only the stack and the read/write portion of the data segment of a program are writable, while read-only data and the code segment are not writable. Thus attempting to read outside of the program’s address space, or writing to a read-only segment of the address space, results in a segmentation fault, hence the name.
On systems using hardware memory segmentation to provide virtual memory, a segmentation fault occurs when the hardware detects an attempt to refer to a non-existent segment, or to refer to a location outside the bounds of a segment, or to refer to a location in a fashion not allowed by the permissions granted for that segment. On systems using only paging, an invalid page fault generally leads to a segmentation fault, and segmentation faults and page faults are both faults raised by the virtual memory management system. Segmentation faults can also occur independently of page faults: illegal access to a valid page is a segmentation fault, but not an invalid page fault, and segmentation faults can occur in the middle of a page (hence no page fault), for example in a buffer overflow that stays within a page but illegally overwrites memory.
At the hardware level, the fault is initially raised by the memory management unit (MMU) on illegal access (if the referenced memory exists), as part of its memory protection feature, or an invalid page fault (if the referenced memory does not exist). If the problem is not an invalid logical address but instead an invalid physical address, a bus error is raised instead, though these are not always distinguished.
At the operating system level, this fault is caught and a signal is passed on to the offending process, activating the process’s handler for that signal. Different operating systems have different signal names to indicate that a segmentation fault has occurred. On Unix-like operating systems, a signal called SIGSEGV (abbreviated from segmentation violation) is sent to the offending process. On Microsoft Windows, the offending process receives a STATUS_ACCESS_VIOLATION exception.
Causes[edit]
The conditions under which segmentation violations occur and how they manifest themselves are specific to hardware and the operating system: different hardware raises different faults for given conditions, and different operating systems convert these to different signals that are passed on to processes. The proximate cause is a memory access violation, while the underlying cause is generally a software bug of some sort. Determining the root cause – debugging the bug – can be simple in some cases, where the program will consistently cause a segmentation fault (e.g., dereferencing a null pointer), while in other cases the bug can be difficult to reproduce and depend on memory allocation on each run (e.g., dereferencing a dangling pointer).
The following are some typical causes of a segmentation fault:
- Attempting to access a nonexistent memory address (outside process’s address space)
- Attempting to access memory the program does not have rights to (such as kernel structures in process context)
- Attempting to write read-only memory (such as code segment)
These in turn are often caused by programming errors that result in invalid memory access:
- Dereferencing a null pointer, which usually points to an address that’s not part of the process’s address space
- Dereferencing or assigning to an uninitialized pointer (wild pointer, which points to a random memory address)
- Dereferencing or assigning to a freed pointer (dangling pointer, which points to memory that has been freed/deallocated/deleted)
- A buffer overflow
- A stack overflow
- Attempting to execute a program that does not compile correctly. (Some compilers[which?] will output an executable file despite the presence of compile-time errors.)
In C code, segmentation faults most often occur because of errors in pointer use, particularly in C dynamic memory allocation. Dereferencing a null pointer, which results in undefined behavior, will usually cause a segmentation fault. This is because a null pointer cannot be a valid memory address. On the other hand, wild pointers and dangling pointers point to memory that may or may not exist, and may or may not be readable or writable, and thus can result in transient bugs. For example:
char *p1 = NULL; // Null pointer char *p2; // Wild pointer: not initialized at all. char *p3 = malloc(10 * sizeof(char)); // Initialized pointer to allocated memory // (assuming malloc did not fail) free(p3); // p3 is now a dangling pointer, as memory has been freed
Dereferencing any of these variables could cause a segmentation fault: dereferencing the null pointer generally will cause a segfault, while reading from the wild pointer may instead result in random data but no segfault, and reading from the dangling pointer may result in valid data for a while, and then random data as it is overwritten.
Handling[edit]
The default action for a segmentation fault or bus error is abnormal termination of the process that triggered it. A core file may be generated to aid debugging, and other platform-dependent actions may also be performed. For example, Linux systems using the grsecurity patch may log SIGSEGV signals in order to monitor for possible intrusion attempts using buffer overflows.
On some systems, like Linux and Windows, it is possible for the program itself to handle a segmentation fault.[7] Depending on the architecture and operating system, the running program can not only handle the event but may extract some information about its state like getting a stack trace, processor register values, the line of the source code when it was triggered, memory address that was invalidly accessed[8] and whether the action was a read or a write.[9]
Although a segmentation fault generally means that the program has a bug that needs fixing, it is also possible to intentionally cause such failure for the purposes of testing, debugging and also to emulate platforms where direct access to memory is needed. On the latter case, the system must be able to allow the program to run even after the fault occurs. In this case, when the system allows, it is possible to handle the event and increment the processor program counter to «jump» over the failing instruction to continue the execution.[10]
Examples[edit]
Segmentation fault on an EMV keypad
Writing to read-only memory[edit]
Writing to read-only memory raises a segmentation fault. At the level of code errors, this occurs when the program writes to part of its own code segment or the read-only portion of the data segment, as these are loaded by the OS into read-only memory.
Here is an example of ANSI C code that will generally cause a segmentation fault on platforms with memory protection. It attempts to modify a string literal, which is undefined behavior according to the ANSI C standard. Most compilers will not catch this at compile time, and instead compile this to executable code that will crash:
int main(void) { char *s = "hello world"; *s = 'H'; }
When the program containing this code is compiled, the string «hello world» is placed in the rodata section of the program executable file: the read-only section of the data segment. When loaded, the operating system places it with other strings and constant data in a read-only segment of memory. When executed, a variable, s, is set to point to the string’s location, and an attempt is made to write an H character through the variable into the memory, causing a segmentation fault. Compiling such a program with a compiler that does not check for the assignment of read-only locations at compile time, and running it on a Unix-like operating system produces the following runtime error:
$ gcc segfault.c -g -o segfault $ ./segfault Segmentation fault
Backtrace of the core file from GDB:
Program received signal SIGSEGV, Segmentation fault. 0x1c0005c2 in main () at segfault.c:6 6 *s = 'H';
This code can be corrected by using an array instead of a character pointer, as this allocates memory on stack and initializes it to the value of the string literal:
char s[] = "hello world"; s[0] = 'H'; // equivalently, *s = 'H';
Even though string literals should not be modified (this has undefined behavior in the C standard), in C they are of static char [] type,[11][12][13] so there is no implicit conversion in the original code (which points a char * at that array), while in C++ they are of static const char [] type, and thus there is an implicit conversion, so compilers will generally catch this particular error.
Null pointer dereference[edit]
In C and C-like languages, null pointers are used to mean «pointer to no object» and as an error indicator, and dereferencing a null pointer (a read or write through a null pointer) is a very common program error. The C standard does not say that the null pointer is the same as the pointer to memory address 0, though that may be the case in practice. Most operating systems map the null pointer’s address such that accessing it causes a segmentation fault. This behavior is not guaranteed by the C standard. Dereferencing a null pointer is undefined behavior in C, and a conforming implementation is allowed to assume that any pointer that is dereferenced is not null.
int *ptr = NULL; printf("%d", *ptr);
This sample code creates a null pointer, and then tries to access its value (read the value). Doing so causes a segmentation fault at runtime on many operating systems.
Dereferencing a null pointer and then assigning to it (writing a value to a non-existent target) also usually causes a segmentation fault:
int *ptr = NULL; *ptr = 1;
The following code includes a null pointer dereference, but when compiled will often not result in a segmentation fault, as the value is unused and thus the dereference will often be optimized away by dead code elimination:
Buffer overflow[edit]
The following code accesses the character array s beyond its upper boundary. Depending on the compiler and the processor, this may result in a segmentation fault.
char s[] = "hello world"; char c = s[20];
Stack overflow[edit]
Another example is recursion without a base case:
int main(void) { return main(); }
which causes the stack to overflow which results in a segmentation fault.[14] Infinite recursion may not necessarily result in a stack overflow depending on the language, optimizations performed by the compiler and the exact structure of a code. In this case, the behavior of unreachable code (the return statement) is undefined, so the compiler can eliminate it and use a tail call optimization that might result in no stack usage. Other optimizations could include translating the recursion into iteration, which given the structure of the example function would result in the program running forever, while probably not overflowing its stack.
See also[edit]
- General protection fault
- Storage violation
- Guru Meditation
References[edit]
- ^ Expert C programming: deep C secrets By Peter Van der Linden, page 188
- ^ «The Rust Programming Language — Ownership».
- ^ «Fearless Concurrency with Rust — The Rust Programming Language Blog».
- ^ McCarthy, John (April 1960). «Recursive functions of symbolic expressions and their computation by machine, Part I». Communications of the ACM. 4 (3): 184–195. doi:10.1145/367177.367199. S2CID 1489409. Retrieved 2018-09-22.
- ^ Dhurjati, Dinakar; Kowshik, Sumant; Adve, Vikram; Lattner, Chris (1 January 2003). «Memory Safety Without Runtime Checks or Garbage Collection» (PDF). Proceedings of the 2003 ACM SIGPLAN Conference on Language, Compiler, and Tool for Embedded Systems. ACM. 38 (7): 69–80. doi:10.1145/780732.780743. ISBN 1581136471. S2CID 1459540. Retrieved 2018-09-22.
- ^ «Debugging Segmentation Faults and Pointer Problems — Cprogramming.com». www.cprogramming.com. Retrieved 2021-02-03.
- ^ «Cleanly recovering from Segfaults under Windows and Linux (32-bit, x86)». Retrieved 2020-08-23.
- ^ «Implementation of the SIGSEGV/SIGABRT handler which prints the debug stack trace». GitHub. Retrieved 2020-08-23.
- ^ «How to identify read or write operations of page fault when using sigaction handler on SIGSEGV?(LINUX)». Retrieved 2020-08-23.
- ^ «LINUX – WRITING FAULT HANDLERS». Retrieved 2020-08-23.
- ^ «6.1.4 String literals». ISO/IEC 9899:1990 — Programming languages — C.
- ^ «6.4.5 String literals». ISO/IEC 9899:1999 — Programming languages — C.
- ^ «6.4.5 String literals». ISO/IEC 9899:2011 — Programming languages — C.
- ^ What is the difference between a segmentation fault and a stack overflow? at Stack Overflow
External links[edit]
- Process: focus boundary and segmentation fault[dead link]
- A FAQ: User contributed answers regarding the definition of a segmentation fault
- A «null pointer» explained
- Answer to: NULL is guaranteed to be 0, but the null pointer is not?
- The Open Group Base Specifications Issue 6 signal.h