NPM дает нам возможность использовать флаг –force, то есть npm audit fix –force но NPM предупредит вас об использовании этого флага:
npm audit fix --force
npm WARN using --force I sure hope you know what you are doing.Так что же нам делать?
Если наш менеджер пакетов не может исправить эти уязвимости, то, конечно, нам не повезло, и мы должны найти способ выжить с этими уязвимостями, надеясь, что никто не решит использовать их против нашего проекта.
Исправление
Обновляйте пакеты по одному с помощью команды, предложенной NPM, вместо запуска команды npm audit fix –force.
Например, npm install –save-dev jest@24.8.0.
Прежде всего, я хочу сказать, что это может быть невероятно очевидно для тех, кто сталкивался с этой проблемой раньше.
Когда я впервые увидел всеэ то, это был гигантский список предупреждений, и, будучи ленивым, я даже не удосужился прокрутить список проблем.
Если вы просто продолжите прокручивать внутри своей консоли до самой первой проблемы, вы фактически столкнетесь с исправлением, и да, как и следовало ожидать, это так же просто, как обновить пакет, вызывающий проблему.
npm audit --fix
=== npm audit security report ===
# Run npm install --save-dev jest@24.8.0 to resolve 62 vulnerabilities
SEMVER WARNING: Recommended action is a potentially breaking change
┌───────────────┬──────────────────────────────────────────────────────────────┐
│ Low │ Regular Expression Denial of Service │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Package │ braces │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Dependency of │ jest [dev] │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Path │ jest > jest-cli > jest-config > babel-jest > │
│ │ babel-plugin-istanbul > test-exclude > micromatch > braces │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ More info │ https://nodesecurity.io/advisories/786 │
└───────────────┴──────────────────────────────────────────────────────────────┘
... 61 more vulerabilities ...Прямо перед описанием уязвимости вы увидите текст # Run npm install –save-dev jest@24.8.0 to resolve 62 vulnerabilities чтобы устранить 62 уязвимости, и это именно то, что нам нужно.
Вы также можете заметить, что в следующей строке написано SEMVER WARNING: SEMVER WARNING: Recommended action is a potentially breaking change.
Выполнение этой команды вручную вместо использования иnpm audit fix –force позволяет нам точно знать, какие пакеты мы обновляем.
Это очень полезно для скриптов, в котором обновление этих пакетов действительно приводит к серьезным изменениям.
Заключение
В итоге, ручное обновление уязвимых пакетов и запуск исправления аудита npm –force даст те же результаты.
Единственное отличие состоит в том, что ручное обновление наших пакетов позволит нам обновить один пакет, протестировать на наличие критических изменений, а затем обновить следующий пакет, вместо того, чтобы просто обновить все пакеты сразу, найти критическое изменение и не иметь представления какой пакет решил все испортить.
I’m very wondered that I can’t find an answer to this simple question. Also I’m very wondered that npm update does not solve this.
I can’t post my complete dependency tree here but let me describe my issue anyway:
minimist is outdated (version 1.2.0) and has a security vulnerability in this version. The packages require minimist define the dependency as ^1.2.0 — so it is compatible with 1.2.2.
The common solution is to put it to package.json within devDependencies or dependencies with ^1.2.2. I don’t want to put it into package.json. I feel like npm update should also update indirect dependencies.
Am I missing something?
Here you can see my package-lock.json: https://github.com/tflori/riki-community/blob/master/package-lock.json
And the output of npm ls minimist:
riki-community@ /home/iras/work/projects/riki/community
├─┬ awesome-typescript-loader@5.2.1
│ ├─┬ loader-utils@1.2.3
│ │ └─┬ json5@1.0.1
│ │ └── minimist@1.2.0 deduped
│ └─┬ mkdirp@0.5.1
│ └── minimist@0.0.8
├─┬ jest@25.1.0
│ └─┬ @jest/core@25.1.0
│ ├─┬ @jest/transform@25.1.0
│ │ └─┬ @babel/core@7.8.7
│ │ └─┬ json5@2.1.2
│ │ └── minimist@1.2.5
│ └─┬ jest-haste-map@25.1.0
│ └─┬ sane@4.1.0
│ ├─┬ @cnakazawa/watch@1.0.4
│ │ └── minimist@1.2.0 deduped
│ └── minimist@1.2.0 deduped
├─┬ node-sass@4.13.1
│ └─┬ meow@3.7.0
│ └── minimist@1.2.0
├─┬ ts-jest@25.2.1
│ └─┬ json5@2.1.2
│ └── minimist@1.2.5
├─┬ tsconfig-paths-webpack-plugin@3.2.0
│ └─┬ tsconfig-paths@3.8.0
│ └── minimist@1.2.0 deduped
└─┬ webpack@4.42.0
└─┬ watchpack@1.6.0
└─┬ chokidar@2.1.8
└─┬ UNMET OPTIONAL DEPENDENCY fsevents@1.2.9
└─┬ UNMET OPTIONAL DEPENDENCY node-pre-gyp@0.12.0
├─┬ UNMET OPTIONAL DEPENDENCY mkdirp@0.5.1
│ └── UNMET OPTIONAL DEPENDENCY minimist@0.0.8
└─┬ UNMET OPTIONAL DEPENDENCY rc@1.2.8
└── UNMET OPTIONAL DEPENDENCY minimist@1.2.0
asked Mar 17, 2020 at 9:23
3
Your best bet is to update npm to version >= 7.0. Please see the answer from xeos for more details. If that is not possible there are two solutions:
The problem is the depth. From the documentation:
As of npm@2.6.1, the npm update will only inspect top-level packages. Prior versions of npm would also recursively inspect all dependencies. To get the old behavior, use npm —depth 9999 update.
So we have to provide the depth that we want to update. In my case, the 9999 depth took too long and I cancelled it. But a --depth 5 was enough.
npm update --depth 5
If that does still not update the dependency then you have to manually change the package-lock.json.
Open the package-lock.json and find all occurrences of "minimist": { and remove the object.
Example:
Change this:
"dependencies": {
"minimist": {
"version": "1.2.0",
"bundled": true,
"dev": true,
"optional": true
}
}
to that:
"dependencies": {
}
And run npm install again.
answered Mar 17, 2020 at 16:01
iRaSiRaS
1,8781 gold badge16 silver badges28 bronze badges
2
As of npm v7.0.0, running npm update will always update all packages, not just the ones specified in root package.json file. NPM has removed --depth option from npm update command and changed its behavior.
Note: it is still possible that some underlying package is specifying an outdated version as a dependency, which will prevent npm update from installing the latest version. You don’t have many options, other than forcing a resolution to a more recent version.
answered Nov 13, 2021 at 0:30
XeosXeos
5,70511 gold badges47 silver badges79 bronze badges
4
I also needed to manually change the minimist version to «^1.2.5» from «0.0.8» for the dependency of «mkdirp»
answered Mar 17, 2020 at 15:35
JamesJames
511 silver badge4 bronze badges
If you want to update all dependencies recursively, I believe this is the fastest, most robust solution:
First, make sure you commit any changes in case you run into problems with git commit package*.json. Second, update any of your direct dependencies as desired with npm outdated and npm update xyz
Now, update all package versions with a clean build of package-lock.json:
# remove current node_modules/ and package-lock.json
rm -rf package-lock.json node_modules/
# rebuild package-lock.json the the semantically-compatible
# latest package versions & install node_modules/
npm install
# ensure nothing broke
npm test
If there is a problem, roll back:
rm -rf package-lock.json node_modules/
git checkout package*.json
npm install
P.S. This technique has worked well for me, but I’m always learning more about NPM & package-lock. I’d love to hear from other NPM experts on this technique.
answered Sep 16, 2020 at 16:38
1
I’m very wondered that I can’t find an answer to this simple question. Also I’m very wondered that npm update does not solve this.
I can’t post my complete dependency tree here but let me describe my issue anyway:
minimist is outdated (version 1.2.0) and has a security vulnerability in this version. The packages require minimist define the dependency as ^1.2.0 — so it is compatible with 1.2.2.
The common solution is to put it to package.json within devDependencies or dependencies with ^1.2.2. I don’t want to put it into package.json. I feel like npm update should also update indirect dependencies.
Am I missing something?
Here you can see my package-lock.json: https://github.com/tflori/riki-community/blob/master/package-lock.json
And the output of npm ls minimist:
riki-community@ /home/iras/work/projects/riki/community
├─┬ awesome-typescript-loader@5.2.1
│ ├─┬ loader-utils@1.2.3
│ │ └─┬ json5@1.0.1
│ │ └── minimist@1.2.0 deduped
│ └─┬ mkdirp@0.5.1
│ └── minimist@0.0.8
├─┬ jest@25.1.0
│ └─┬ @jest/core@25.1.0
│ ├─┬ @jest/transform@25.1.0
│ │ └─┬ @babel/core@7.8.7
│ │ └─┬ json5@2.1.2
│ │ └── minimist@1.2.5
│ └─┬ jest-haste-map@25.1.0
│ └─┬ sane@4.1.0
│ ├─┬ @cnakazawa/watch@1.0.4
│ │ └── minimist@1.2.0 deduped
│ └── minimist@1.2.0 deduped
├─┬ node-sass@4.13.1
│ └─┬ meow@3.7.0
│ └── minimist@1.2.0
├─┬ ts-jest@25.2.1
│ └─┬ json5@2.1.2
│ └── minimist@1.2.5
├─┬ tsconfig-paths-webpack-plugin@3.2.0
│ └─┬ tsconfig-paths@3.8.0
│ └── minimist@1.2.0 deduped
└─┬ webpack@4.42.0
└─┬ watchpack@1.6.0
└─┬ chokidar@2.1.8
└─┬ UNMET OPTIONAL DEPENDENCY fsevents@1.2.9
└─┬ UNMET OPTIONAL DEPENDENCY node-pre-gyp@0.12.0
├─┬ UNMET OPTIONAL DEPENDENCY mkdirp@0.5.1
│ └── UNMET OPTIONAL DEPENDENCY minimist@0.0.8
└─┬ UNMET OPTIONAL DEPENDENCY rc@1.2.8
└── UNMET OPTIONAL DEPENDENCY minimist@1.2.0
asked Mar 17, 2020 at 9:23
3
Your best bet is to update npm to version >= 7.0. Please see the answer from xeos for more details. If that is not possible there are two solutions:
The problem is the depth. From the documentation:
As of npm@2.6.1, the npm update will only inspect top-level packages. Prior versions of npm would also recursively inspect all dependencies. To get the old behavior, use npm —depth 9999 update.
So we have to provide the depth that we want to update. In my case, the 9999 depth took too long and I cancelled it. But a --depth 5 was enough.
npm update --depth 5
If that does still not update the dependency then you have to manually change the package-lock.json.
Open the package-lock.json and find all occurrences of "minimist": { and remove the object.
Example:
Change this:
"dependencies": {
"minimist": {
"version": "1.2.0",
"bundled": true,
"dev": true,
"optional": true
}
}
to that:
"dependencies": {
}
And run npm install again.
answered Mar 17, 2020 at 16:01
iRaSiRaS
1,8781 gold badge16 silver badges28 bronze badges
2
As of npm v7.0.0, running npm update will always update all packages, not just the ones specified in root package.json file. NPM has removed --depth option from npm update command and changed its behavior.
Note: it is still possible that some underlying package is specifying an outdated version as a dependency, which will prevent npm update from installing the latest version. You don’t have many options, other than forcing a resolution to a more recent version.
answered Nov 13, 2021 at 0:30
XeosXeos
5,70511 gold badges47 silver badges79 bronze badges
4
I also needed to manually change the minimist version to «^1.2.5» from «0.0.8» for the dependency of «mkdirp»
answered Mar 17, 2020 at 15:35
JamesJames
511 silver badge4 bronze badges
If you want to update all dependencies recursively, I believe this is the fastest, most robust solution:
First, make sure you commit any changes in case you run into problems with git commit package*.json. Second, update any of your direct dependencies as desired with npm outdated and npm update xyz
Now, update all package versions with a clean build of package-lock.json:
# remove current node_modules/ and package-lock.json
rm -rf package-lock.json node_modules/
# rebuild package-lock.json the the semantically-compatible
# latest package versions & install node_modules/
npm install
# ensure nothing broke
npm test
If there is a problem, roll back:
rm -rf package-lock.json node_modules/
git checkout package*.json
npm install
P.S. This technique has worked well for me, but I’m always learning more about NPM & package-lock. I’d love to hear from other NPM experts on this technique.
answered Sep 16, 2020 at 16:38
1
May 13, 2020
javascript npm yarn security vulnerability english
Intro
Not so long ago Github introduced security alerts:
So lot of developers started to use in their applications to make them secure. However we still facing with issues that 3rd party packages from your package.json dependecies have vulnerabilities. So it that case it’s not so obvious how to fix that issues.
But we have some options how to fix them.
NPM/Yarn update
npm update or yarn update
This is the simplest way to fix security issue, but sometimes it will doesn’t work because it may cause updates to many packages and as result deep testing of your app.
NPM packages
If you are using npm greater than 6 version, so you can use pretty good intrument like:
Show only potential vulnerabilities in your dependecies:
npm audit
Execute vulnerabilities fix mechanism:
npm audit fix
- remove
node_modulesbefore run this command - Do not recomend you to use
--forceflag here, because in that casenpm auditwill override some deps which might be not compatible with existing ones.
Yarn packages
Yarn also has yarn audit mechanism, but it hasn’t yarn audit fix mechanism. So in most cases you have to fix these issues manually. So how it works. As example will demonstrate it for minimist package:
-
Add a resolutions key in your
package.jsonfile:- This resolution will override minimist entirely your project.
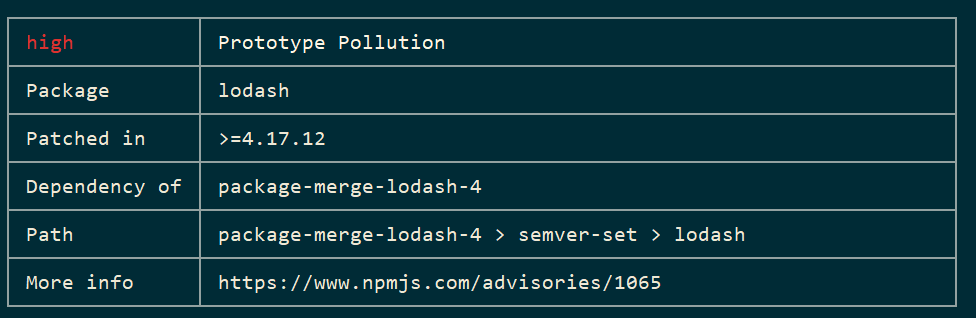
{ "resolutions": { "minimist": "^1.2.5" } }- But in most cases that changes could break your app, so I would suggest to use better case. Let’s see how it works on example of
package-merge-lodash-4package. Audit says that[email protected]has vulnerabilities.
Also we can check them here https://snyk.io/test/npm/lodash/3.9.3. And this resource suggest us to upgrade[email protected] -> 4.17.12. So let’s do it:
{ "resolutions": { "package-merge-lodash-4/*/lodash": "4.17.12" }, }
- Use
npm-force-resolutions(https://www.npmjs.com/package/npm-force-resolutions) by addingpreinstallcommand under"script"category:
"scripts": {
"preinstall": "npx npm-force-resolutions"
}
- Run
npm install.
That’s it. It will update your package-lock.json/yarn.lock files accordingly. That solves the dependency issues which can not be updated using either npm update or by uninstalling and reinstalling a new dependency.
In case of overriding all version of minimist to v1.2.5 yarn.lock will look like:
[email protected], [email protected], [email protected]^1.1.0, [email protected]^1.1.1, [email protected]^1.1.3, [email protected]^1.2.0, [email protected]^1.2.5, [email protected]~0.0.1:
version "1.2.5"
resolved "https://registry.yarnpkg.com/minimist/-/minimist-1.2.5.tgz#67d66014b66a6a8aaa0c083c5fd58df4e4e97602"
integrity sha512-FM9nNUYrRBAELZQT3xeZQ7fmMOBg6nWNmJKTcgsJeaLstP/UODVpGsr5OhXhhXg6f+qtJ8uiZ+PUxkDWcgIXLw==
In case of lodash our yarn.lock will contains following lines:
[email protected], [email protected]^3.9.3:
version "4.17.12"
resolved "https://registry.yarnpkg.com/lodash/-/lodash-4.17.12.tgz#a712c74fdc31f7ecb20fe44f157d802d208097ef"
integrity sha512-+CiwtLnsJhX03p20mwXuvhoebatoh5B3tt+VvYlrPgZC1g36y+RRbkufX95Xa+X4I59aWEacDFYwnJZiyB
Please keep in mind if some packages are only compatible with an older version, then this change might break your app. So be careful while resolving to a particular version and test your app before releasing this change.
Useful links
- npm audit
- yarn audit
- Detailed information and remediation guidance for known vulnerabilities
Happy fix vulnerabilities and make your code safe! ✌🏼
TLDR;
- Run the
npm auditcommand - Scroll until you find a line of text separating two issues
- Manually run the command given in the text to upgrade one package at a time, e.g.
npm i --save-dev jest@24.8.0 - After upgrading a package make sure to check for breaking changes before upgrading the next package
- Avoid running
npm audit fix --force
Vulnerabilities
Every now and then after installing your projects dependencies, npm i, you will be met with an error from NPM that looks something like
┌───────────────┬──────────────────────────────────────────────────────────────┐
│ Low │ Regular Expression Denial of Service │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Package │ braces │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Dependency of │ jest [dev] │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Path │ jest > jest-cli > micromatch > braces │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ More info │ https://nodesecurity.io/advisories/786 │
└───────────────┴──────────────────────────────────────────────────────────────┘
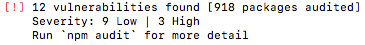
found 62 low severity vulnerabilities in 20610 scanned packages
62 vulnerabilities require semver-major dependency updates.
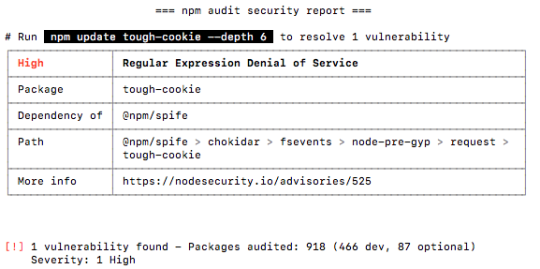
This is actually an extremely small example of a typical vulnerability warning. As you can see from the text underneath the vulnerability it says
found 62 low severity vulnerabilities in 20610 scanned packages
62 vulnerabilities require semver-major dependency updates.
Meaning that this example would have another 61 vulnerabilities ranging from low to high with of course high being the most dangerous vulnerability. For more info on any of these vulnerabilities, there is also a link to the vulnerability on NPM inside the More Info section of the warning.
At first, it may seem confusing on how to properly fix these vulnerabilities. NPM actually provides a service built into NPM that is supposed to automatically fix these issues, npm audit fix, but I’ve found that this will rarely work, and will leave you with nearly just as many vulnerabilities as before. In fact, here’s an example of what happened after I ran npm audit fix.
fixed 0 of 62 vulnerabilities in 20610 scanned packages
1 package update for 62 vulns involved breaking changes
(use `npm audit fix --force` to install breaking changes; or refer to `npm audit` for steps to fix these manually)
NPM gives us the option to use the --force flag, npm audit fix --force, but even NPM will warn you about using this flag
user@group:~/npm_project$ npm audit fix --force
npm WARN using --force I sure hope you know what you are doing.
So what are we supposed to do? If our package manager isn’t able to fix these vulnerabilities then surely we’re out of luck and must find a way to survive with these vulnerabilities hoping nobody decides to exploit them against our project.
The Fix
Manually upgrade the packages one at a time with the command suggested by NPM instead of running the npm audit fix --force command. For example npm install --save-dev jest@24.8.0.
First of all, I want to say that this might be incredibly obvious to those that have run into this problem before. When I first saw these, it was a gigantic list of warnings and being the lazy developer that I am, I didn’t even bother to scroll through the issues.
If you just continue to scroll up inside your console to the very first issue you’ll actually run into a fix and yes, as you would expect, it’s as simple as updating the package that’s causing the issue.
user@group:~/npm_project$ npm audit --fix
=== npm audit security report ===
# Run npm install --save-dev jest@24.8.0 to resolve 62 vulnerabilities
SEMVER WARNING: Recommended action is a potentially breaking change
┌───────────────┬──────────────────────────────────────────────────────────────┐
│ Low │ Regular Expression Denial of Service │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Package │ braces │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Dependency of │ jest [dev] │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ Path │ jest > jest-cli > jest-config > babel-jest > │
│ │ babel-plugin-istanbul > test-exclude > micromatch > braces │
├───────────────┼──────────────────────────────────────────────────────────────┤
│ More info │ https://nodesecurity.io/advisories/786 │
└───────────────┴──────────────────────────────────────────────────────────────┘
... 61 more vulerabilities ...
Right before the vulnerability issue you’ll notice the text # Run npm install --save-dev jest@24.8.0 to resolve 62 vulnerabilities which is exactly what we’re looking for. You may also notice that the very next line says SEMVER WARNING: Recommended action is a potentially breaking change. Manually running this command instead of using the npm audit fix --force command lets us know exactly which packages we’re updating. This is valuable for the scenario where updating these packages actually causes a breaking change.
Summary
So in the end, manually upgrading the vulnerable packages and running npm audit fix --force is going to have the same results. The only difference is that manually upgrading our packages will allow us to upgrade a single package, test for a breaking change, then update the next package, instead of just upgrading all of the packages at once, find a breaking change, then having no idea which package decided to screw things up.
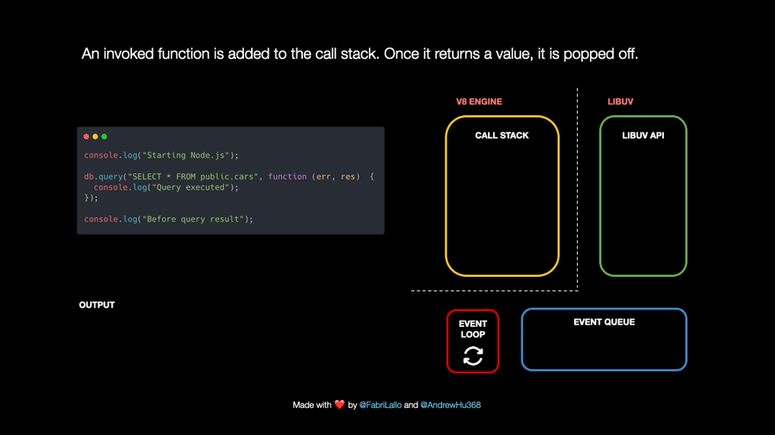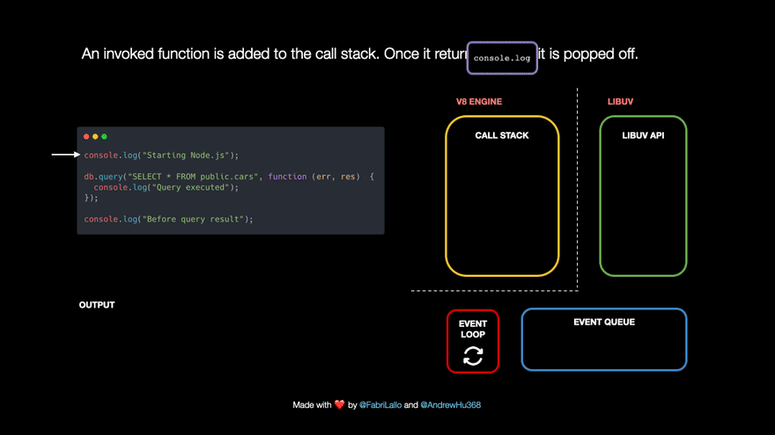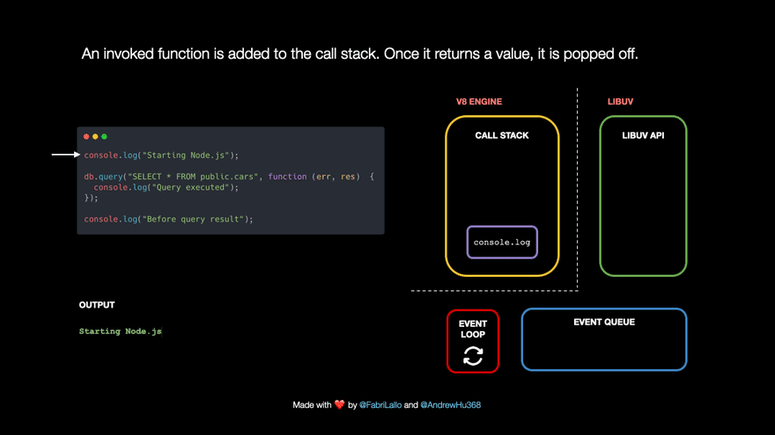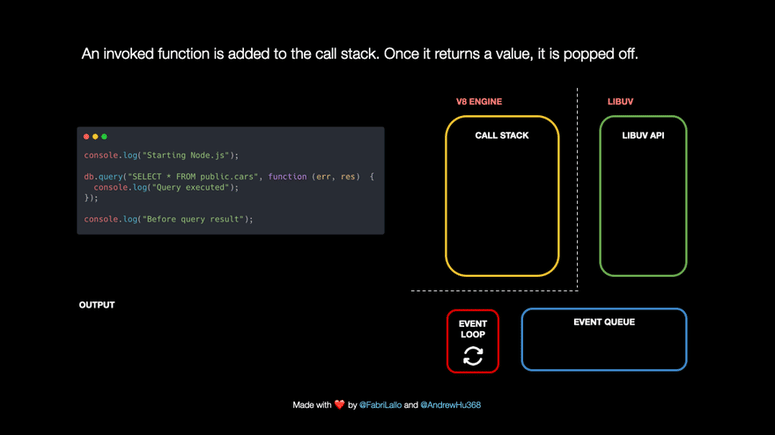
An Animated Guide to Node.js Event Lop
Node.js doesn’t stop from running other operations because of Libuv, a C++ library responsible for the event loop and asynchronously handling tasks such as network requests, DNS resolution, file system operations, data encryption, etc.
What happens under the hood when Node.js works on tasks such as database queries? We will explore it by following this piece of code step by step.
Read next
Create an FAQ Content Type in Drupal 10
Russell Jones — Jan 28
Maximizing Performance: A deep dive into React re-renders and how to optimize your components
olasunkanmi — Jan 27
5 control points to implement serverless integration tests like a boss 👔
Corentin Doue — Feb 8
Completing another Pulp tutorial
Robert Mion — Jan 27
Once unpublished, all posts by bbenefield89 will become hidden and only accessible to themselves.
If bbenefield89 is not suspended, they can still re-publish their posts from their dashboard.
Note:
Once unpublished, this post will become invisible to the public and only accessible to Brandon Benefield.
They can still re-publish the post if they are not suspended.
Thanks for keeping DEV Community 👩💻👨💻 safe. Here is what you can do to flag bbenefield89:
Make all posts by bbenefield89 less visible
bbenefield89 consistently posts content that violates DEV Community 👩💻👨💻’s
code of conduct because it is harassing, offensive or spammy.
Last month, we announced npm@6, which includes a powerful new tool to protect the safety of your code, npm audit. Together with new automatic alerts when a user installs code with a known security risk, audit is a dramatic step to ensure the quality and integrity of the code you use, and protect the world’s largest community of open source software developers.
Read on to learn more about audit and how we’re working to help you develop with confidence.
What is npm audit?
npm audit is a new command that performs a moment-in-time security review of your project’s dependency tree. Audit reports contain information about security vulnerabilities in your dependencies and can help you fix a vulnerability by providing simple-to-run npm commands and recommendations for further troubleshooting.
You can start using npm audit right now by updating to the latest version of npm. Just type npm install npm -g.
Here is an example of running npm audit against your-fantastic-app:
cd your-fantastic-app
npm audit
The results should look like this:
We’ve also built in a summary security report into npm install if vulnerabilities are found during installation:
Or when no vulnerabilities are found:
You can learn more about how to run a security audit on the npm documentation site
What if I’m using a previous version of npm?
npm audit is available in npm@5.10.0 and npm@6. Prior versions of npm will receive vulnerability messages similar to the following:
npm-notice: [SECURITY] marked has 3 high, and 2 moderate vulnerabilities. Go here for more details: [https://nodesecurity.io/advisories?search=marked&version=0.3.0](https://nodesecurity.io/advisories?search=marked&version=0.3.0) - Run `npm i npm@latest -g` to upgrade your npm version, and then `npm audit` to get more info.
We’re not aware of any third-party registry clients that currently support displaying the npm-notify header, so users of these tools will not receive vulnerability messages. For maximum protection against unsafe code, all users should use npm@6.
How does this impact the JavaScript ecosystem?
In the short term, these new alerts and npm audit will raise developers’ awareness of known security vulnerabilities within their applications.They also provide actionable guidance to eliminate the identified risks.
In the longer term, prominent vulnerability warnings and actionable security alerts will raise the floor for everyone. When a developer of a popular package notices they have been bringing in a vulnerable dependency and switches to using a fixed version, instead, every package that depends upon this popular package will now grow safer, too. Everyone stands to benefit from this network effect.
What’s next?
Security is a process, not a project—it’s never done. We will continue to work to improve the security of the npm Registry and the code you write, and we’re excited by what’s in the works in coming weeks and months.
Already, we’ve announced that package signing is on its way. This will allow users of npm packages to verify the integrity of the package regardless of the tools they use to retrieve it or the registry from which they download it.
After this, expect a summer full of products that empower security-focused teams and enterprises by augmenting the tools we’ve announced today. Watch this space.
Update: We’ve added
npm audit fix which combines all the actionable, semver-compatible reports from your audit and runs them for you. You can read more about it in the v6.1.0 release notes.